How to recover data encrypted with eCryptfs
eCryptfs is a widely-applied cryptographic file system that enables selective protection of certain files or directories. While this is a reliable and easy-to-use solution, it may present a challenge when one needs to recover the encrypted items that have been deleted or lost. Without proper decoding, the retrieved data will remain worthless and cannot be accessed even by authorized users. Fortunately, UFS Explorer makes it simple to restore and decrypt files encrypted with eCryptfs as demonstrated in the following guide.
General specifics of eCryptfs
General specifics of eCryptfs
eCryptfs is a popular encryption software package for Linux. It is available in the standard repositories of most of the Linux distributions and is commonly adopted by NAS vendors for encryption of shared folders on devices like Synology, QNAP, Asustor, TerraMaster and others. Instead of encrypting the whole drive, eCryptfs enables protection of individual files and directories that contain sensitive information. It also allows enciphering file and directory names. The cryptographic metadata is stored directly in the file’s header, which makes the encrypted items independent of each other.
The overall process of its deployment is pretty straightforward, and the result will typically look like this:
-
the file’s name consists of a fixed prefix "ECRYPTFS_FNEK_ECRYPTED.", followed by a base64-encoded "Encryption ID" and a base64-encoded encrypted file name;
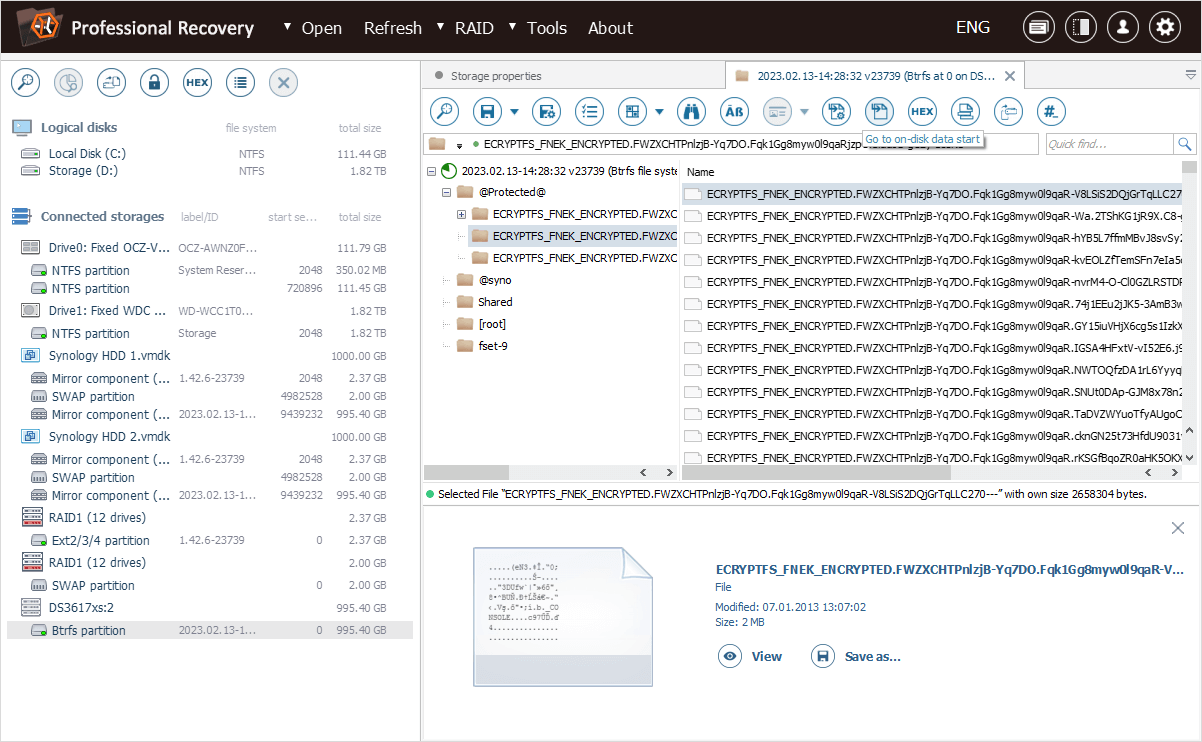
-
the file’s header has a particular format that indicates encryption;
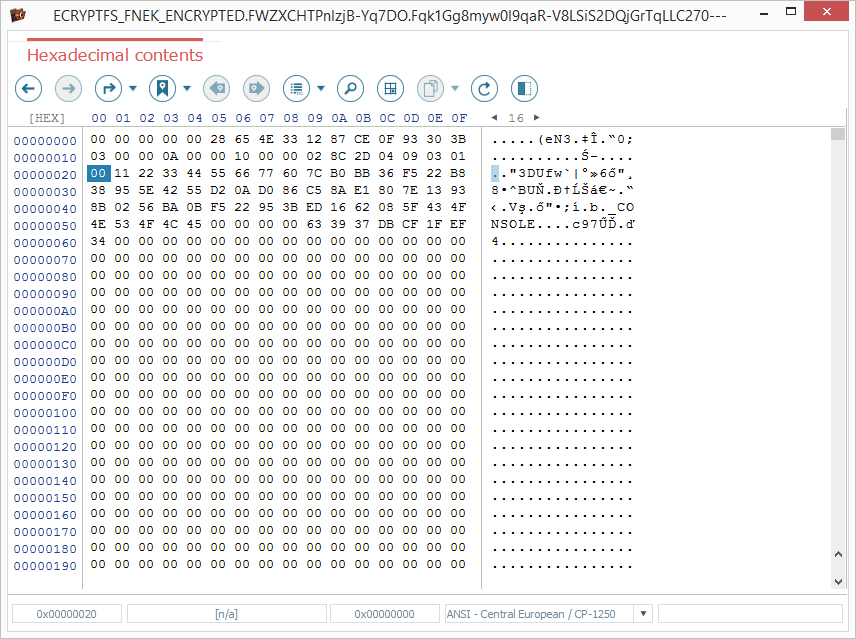
-
the actual file’s content is ciphered.
When such a file falls victim to accidental deletion or other logical mishap that leads to its loss, there is a chance that it may be retrievable using a data recovery utility. Yet, since its data is encrypted, it still has to be unlocked by means of valid credentials. This can be done with a "wrapped-passphrase" file that stores the file encryption key ("encryption passphrase"), or the passphrase itself, which must be kept as a backup copy.
UFS Explorer Professional Recovery features all the functionality necessary to decrypt the data encrypted by eCryptfs of various configurations and enables further smooth work with the obtained content. Let’s have a look how one can deal with different instances of eCryptfs using this data recovery software. Yet, before proceeding, please get familiar with the operating principles of eCryptfs described in a dedicated article.
Files recovery on an encrypted shared folder of a NAS device
In our first illustrative example, we have Synology NAS whose "Protected" shared folder is encrypted with eCryptfs.
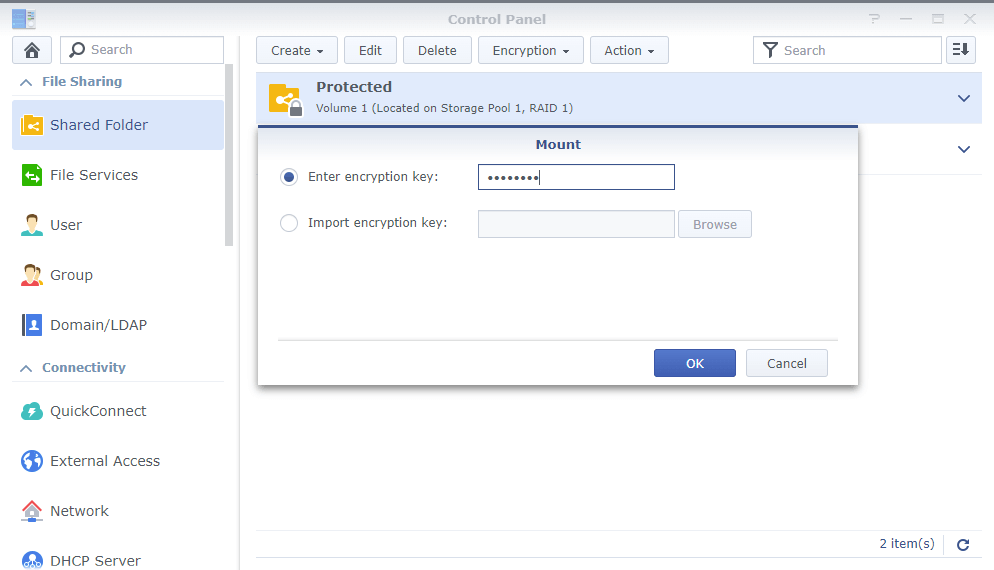
Like most NAS appliances, our unit has a simplified implementation of eCryptfs. It makes use of a fixed standard "wrapping key" as opposed to one generated from the user’s password. This key serves for encryption of the user-defined "encryption passphrase" which, in its turn, is employed to encrypt files on the given shared folder.
The "encryption passphrase" is stored in the "wrapped" form in a special "*.key" file.
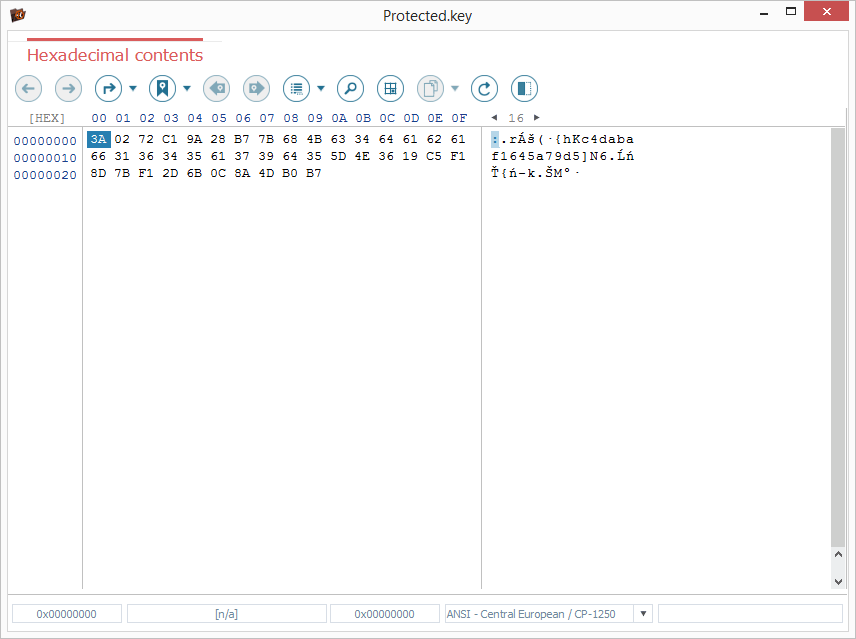
Yet, it must be mentioned that NAS devices from other vendors, for instance, Western Digital may have their own eCryptfs configuration settings and thus decryption specifics. The backup file for their "encryption passphrase" may also have a different format or location.
Decryption of the shared folder on our Synology NAS is possible in case either the correct "encryption passphrase" or the original "*.key" file is available.
Having assembled our storage in the interface of UFS Explorer Professional Recovery using the Synology NAS data recovery recommendations, we can inspect the content of its "data" partition by means of the program.
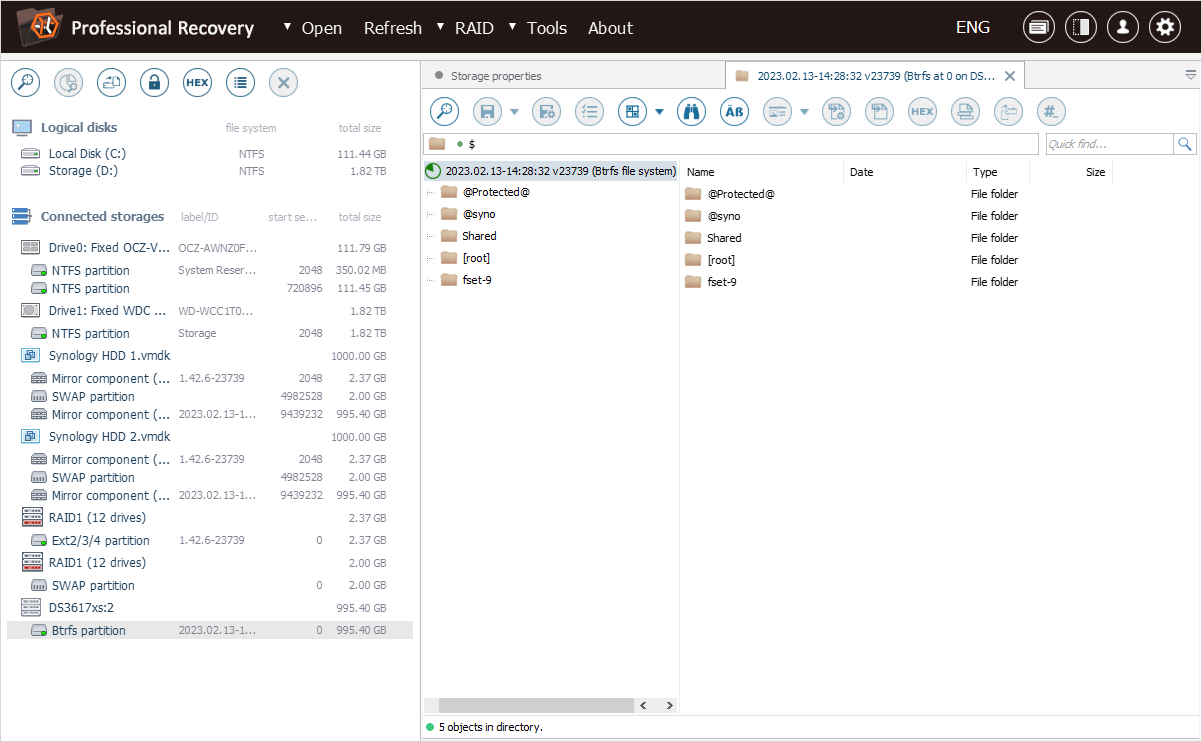
To access the list of shared folders on our NAS, let’s open the "@syno" folder and then go to the "@eaDir" folder.
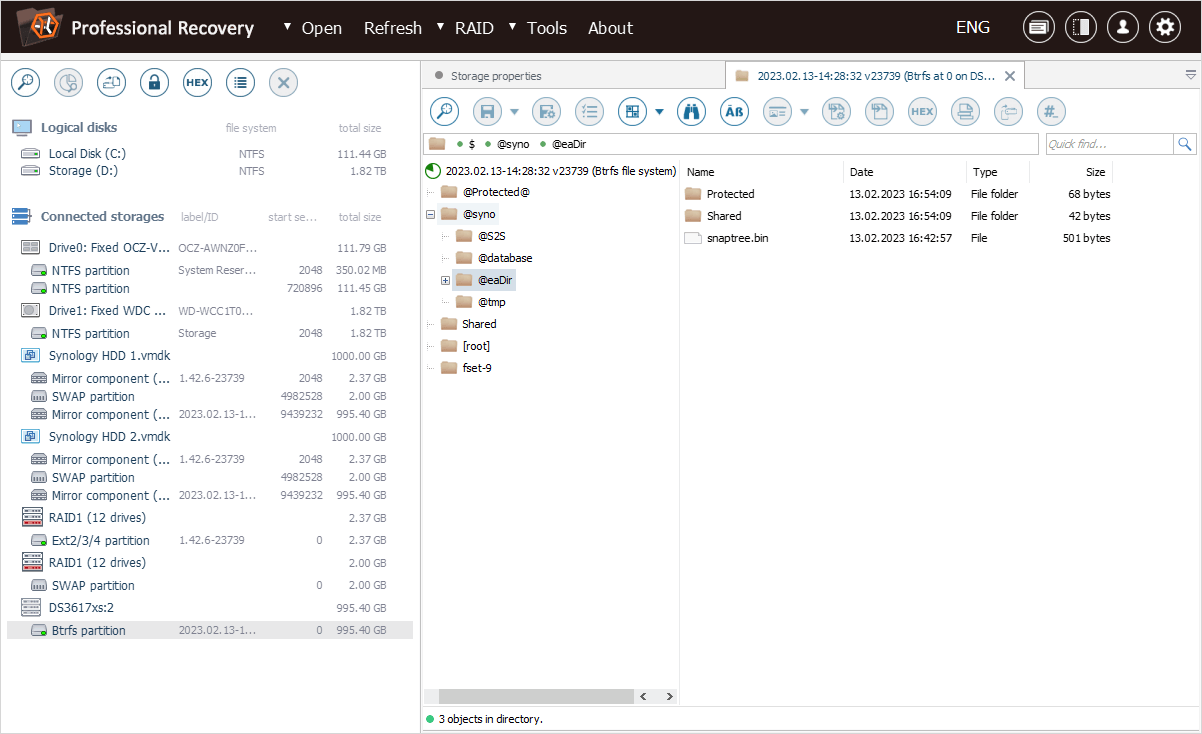
The "SYNO@.encrypt" file found in the folder that corresponds to our "Protected" shared folder reveals that it has been encrypted.
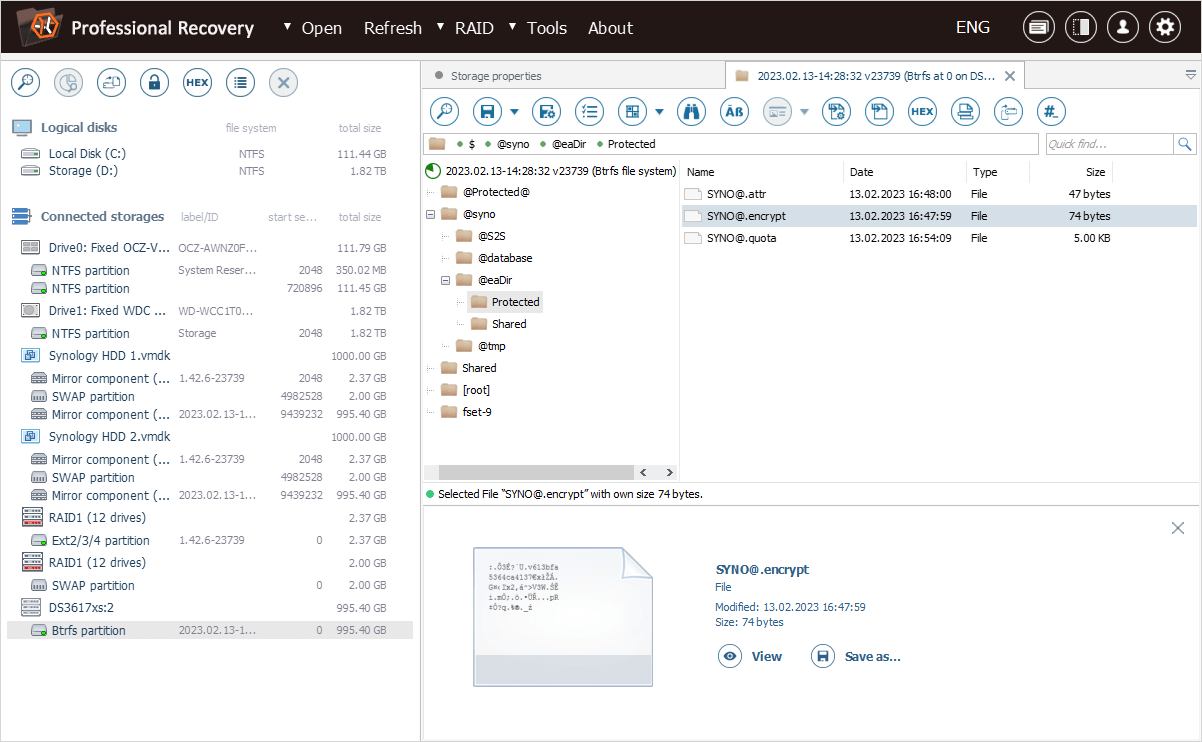
The actual encrypted data is stored in another folder at the root, with the same name, but preceded and followed by the "@" symbol.
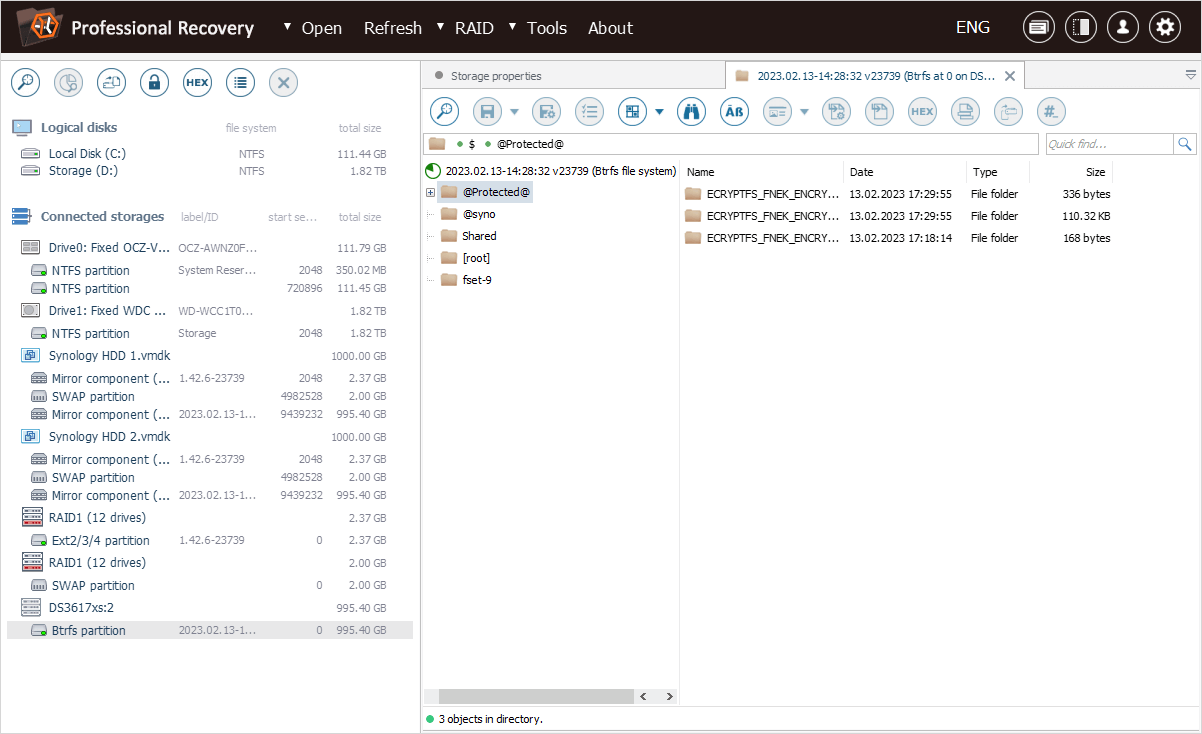
To decrypt the files, we can open the context menu of our file system object and choose the "Transform file system files" option.
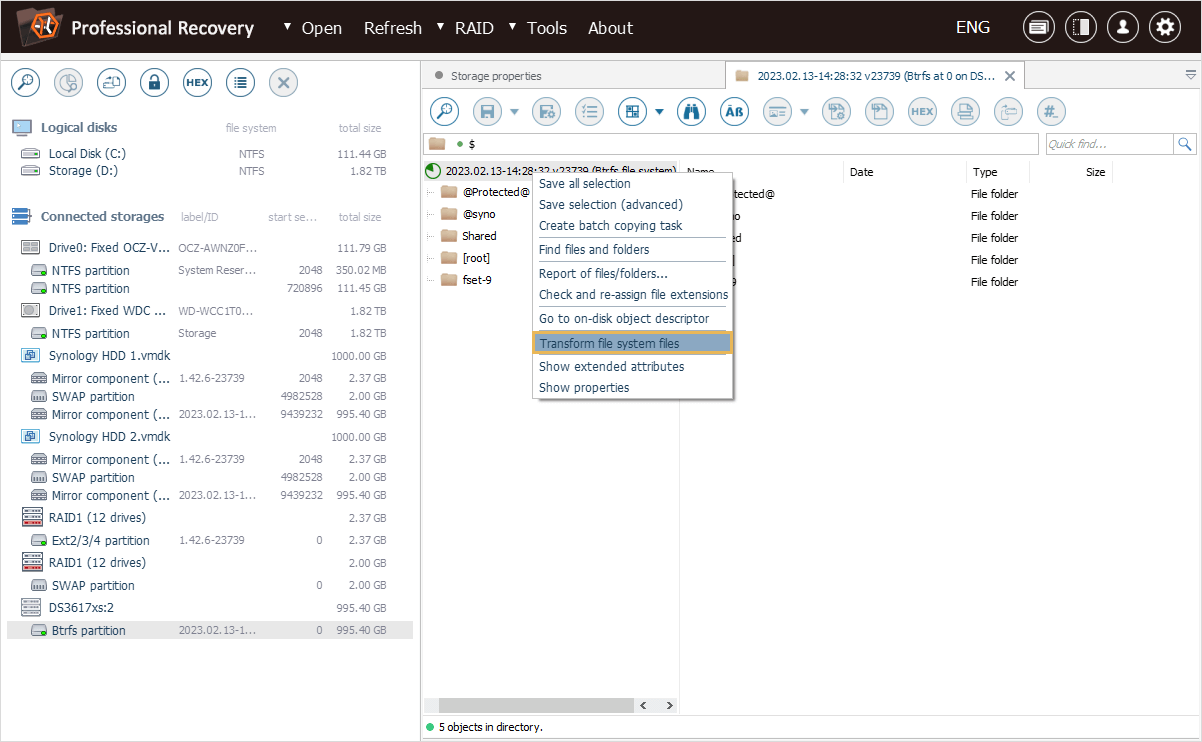
In the opened dialog, we specify the encryption passphrase used upon creation of the shared folder in the "Decryption password" field.
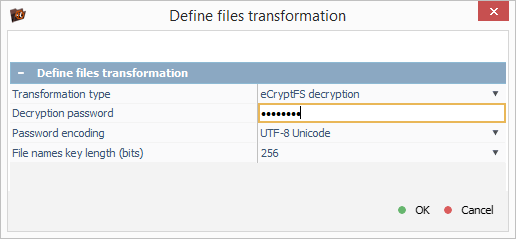
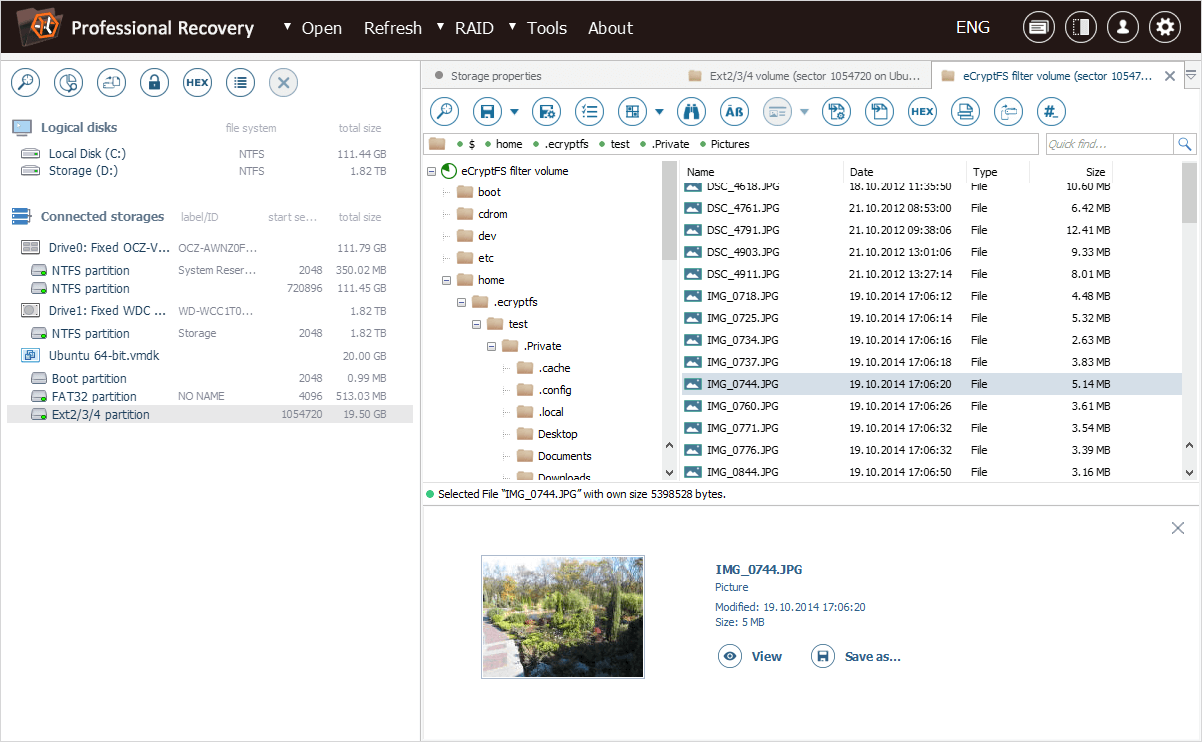
As a result, a new "eCryptfs filter file system" tab appears in the software. This tab contains decrypted files that match the provided password.
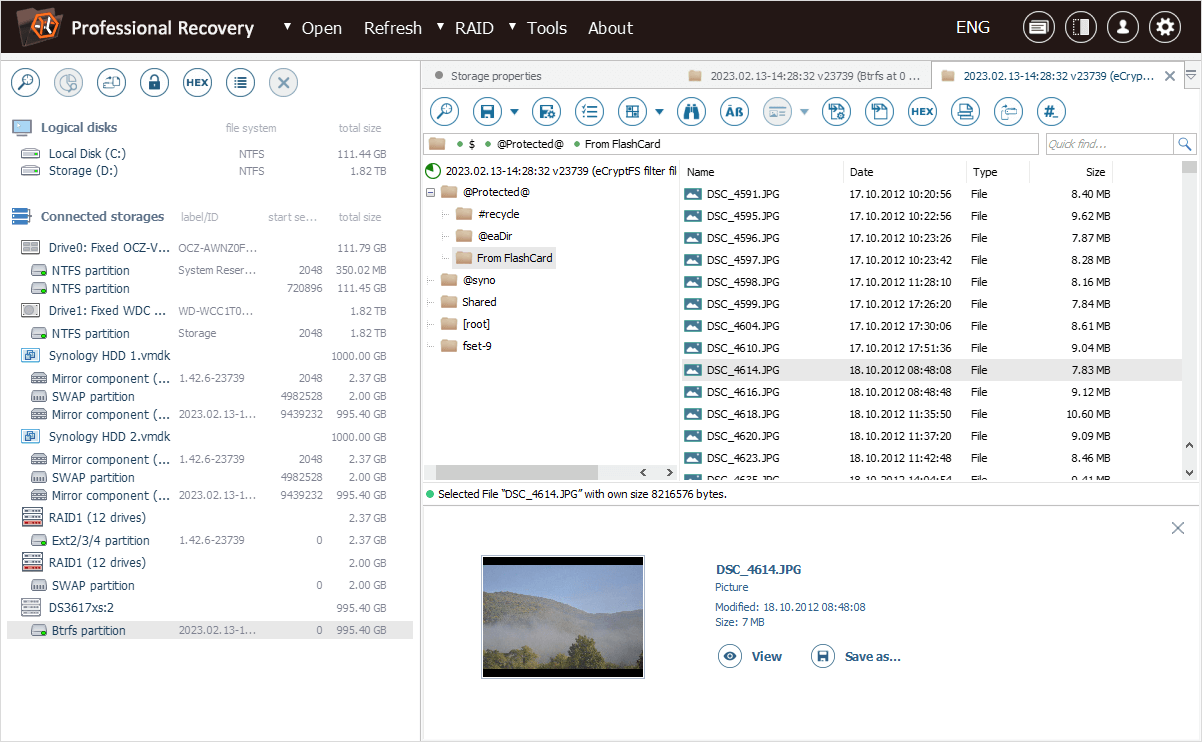
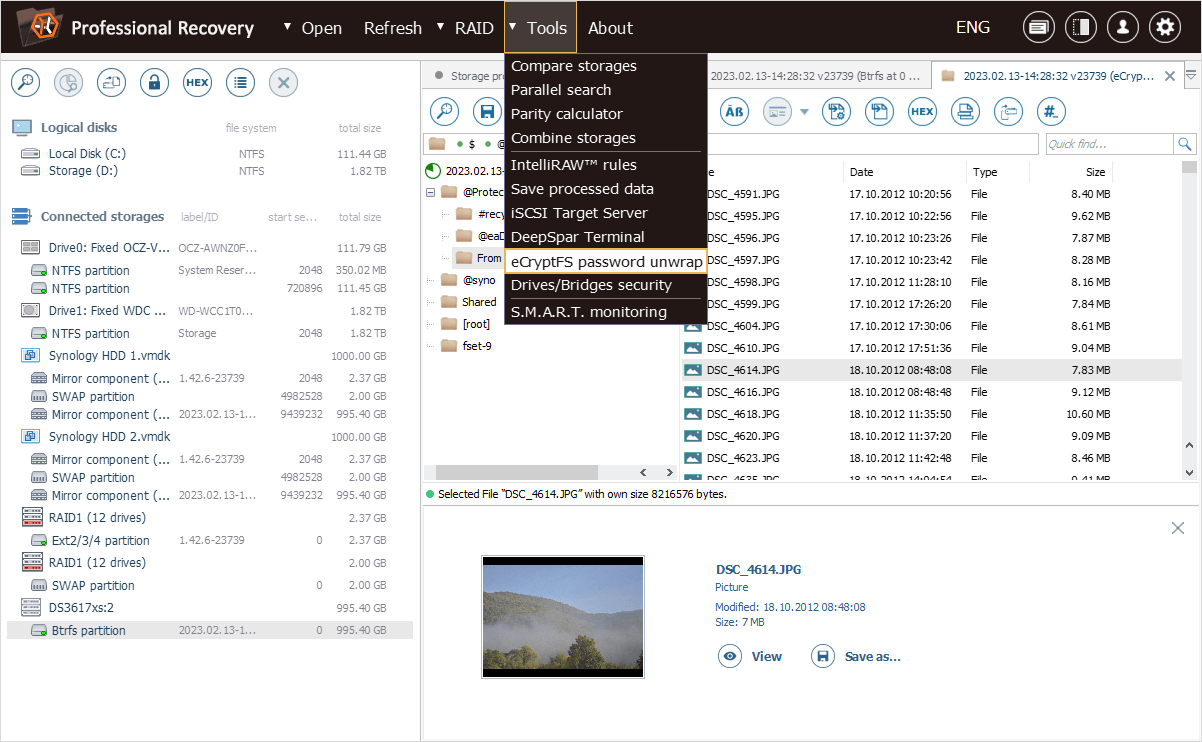
The decryption password, if forgotten, can also be "unwrapped" from the exported backup "*.key" file. For this purpose, the "eCryptfs password unwrap" option is presented in the "Tools" item of the main menu of UFS Explorer Professional Recovery.
In the opened dialog, we set the "Key file path" by navigating to the location of our backup "*.key" file.
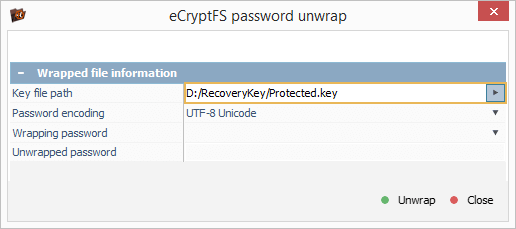
After that, we choose the "Synology NAS default password" option and click "Unwrap" to get our encryption passphrase from this file.
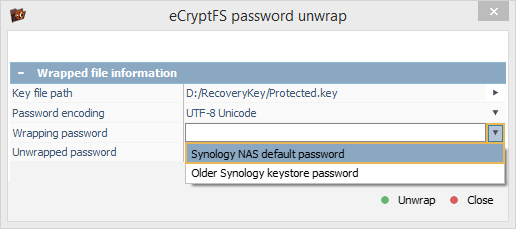
The calculated encryption passphrase can be copied to the clipboard and used for files decryption with the help of the "Transform file system files" option.
Restoring data from an encrypted home folder under Linux
Unlike the majority of NAS platforms, Linux allows encrypting user's home folders by means of a full-featured implementation of eCryptfs. By default, it creates a random file encryption key, and the user’s password is required to "unwrap" it from the "wrapped-passphrase" file. Such an approach enables the system to support the change of the user’s password, but makes things a little more complicated when it comes to the folder’s decryption. It can be performed only on condition that both the user’s password ("login passphrase") and the "wrapped-passphrase" file are available.
Let’s take a look at our Ubuntu sample case. The home folder of the "user" user is not encrypted, while the "test" user has enabled encryption for their home folder.
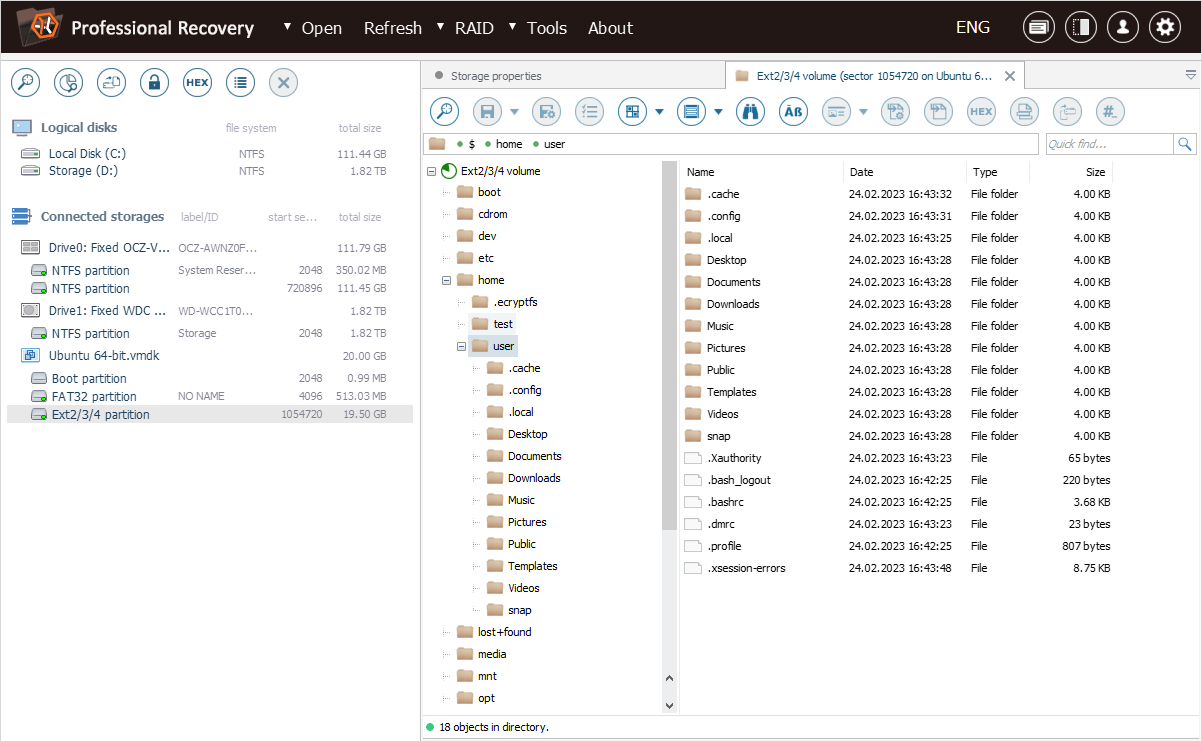
The encrypted content is located in the ".ecryptfs" folder, in the ".Private" subfolder of the folder that corresponds to our "test" user.
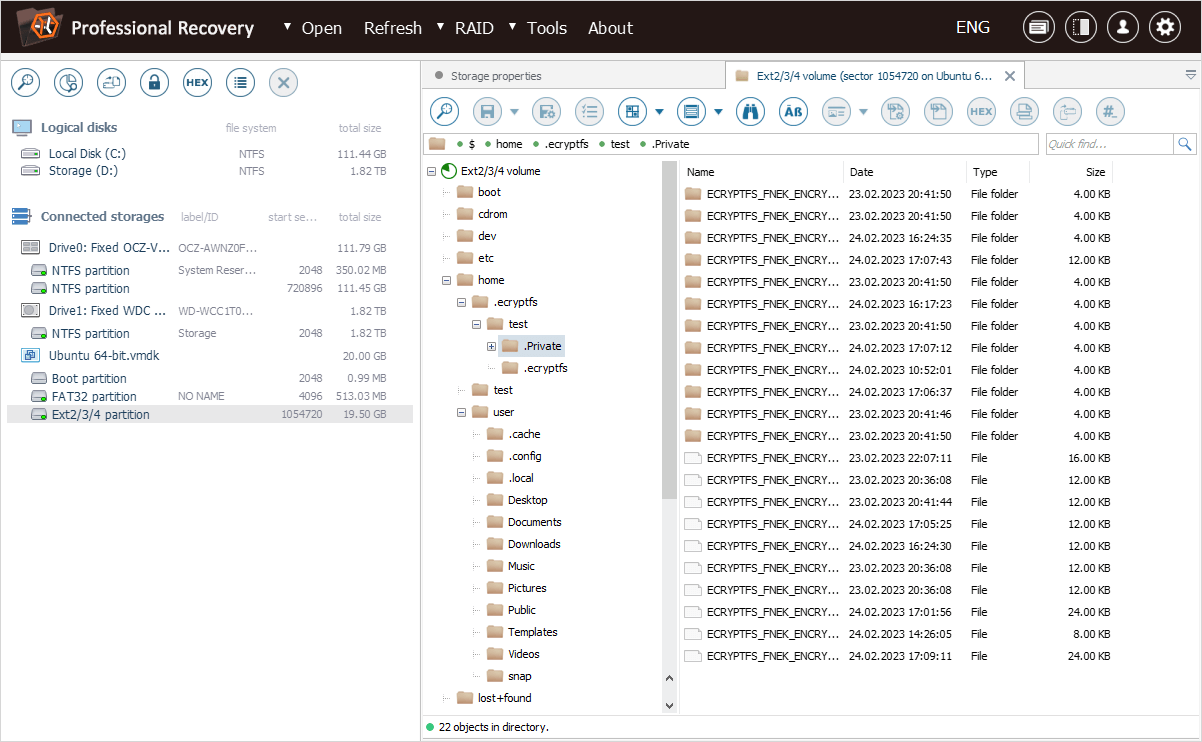
The ".ecryptfs" subfolder contains the "wrapped-passphrase" file. We can save this file to a different location for further extraction of the original encryption key.
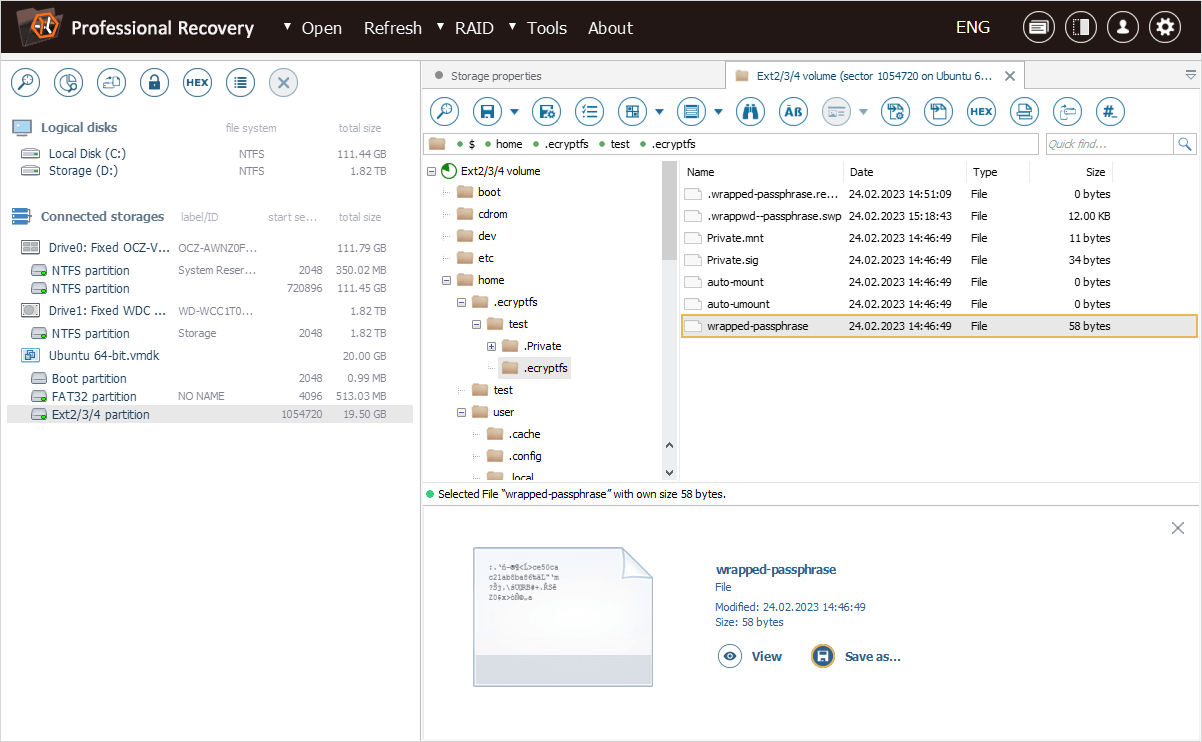
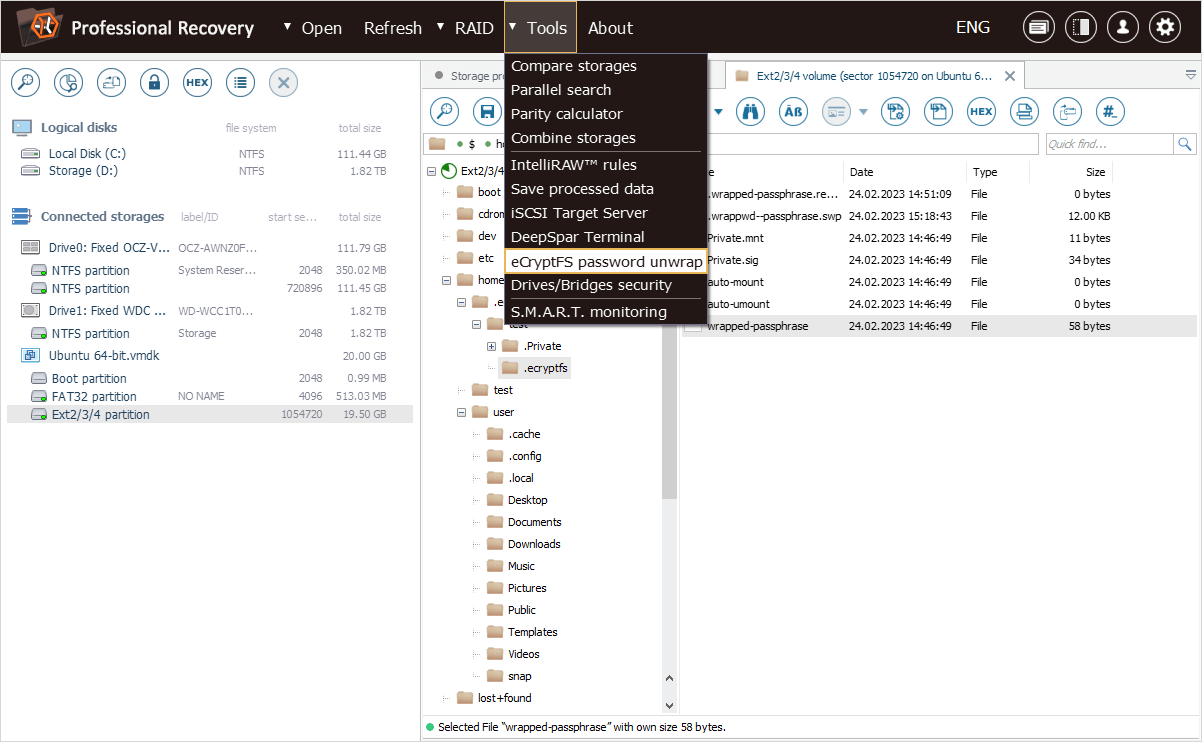
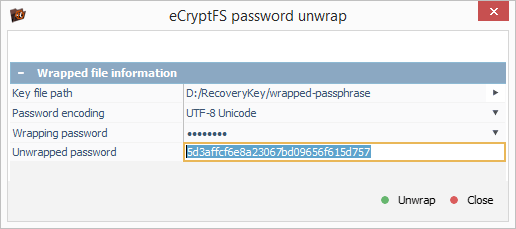
Now we can apply the "eCryptfs password unwrap" option from the "Tools" item of the main menu of UFS Explorer Professional Recovery to "unwrap" the file encryption key from the file.
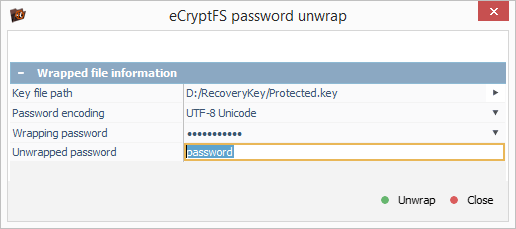
In the opened dialog, we load the "wrapped-passphrase" file using "Key file path" option and then specify the user’s password ("login passphrase") as "Wrapping password" to decrypt the random file encryption key.
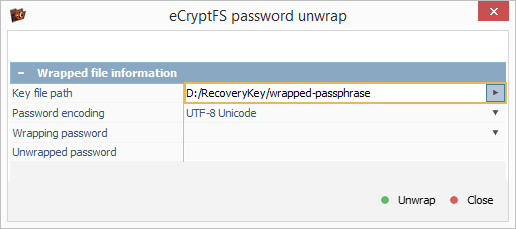
After we press the "Unwrap" button, the program displays the file encryption key that can be copied to the clipboard.
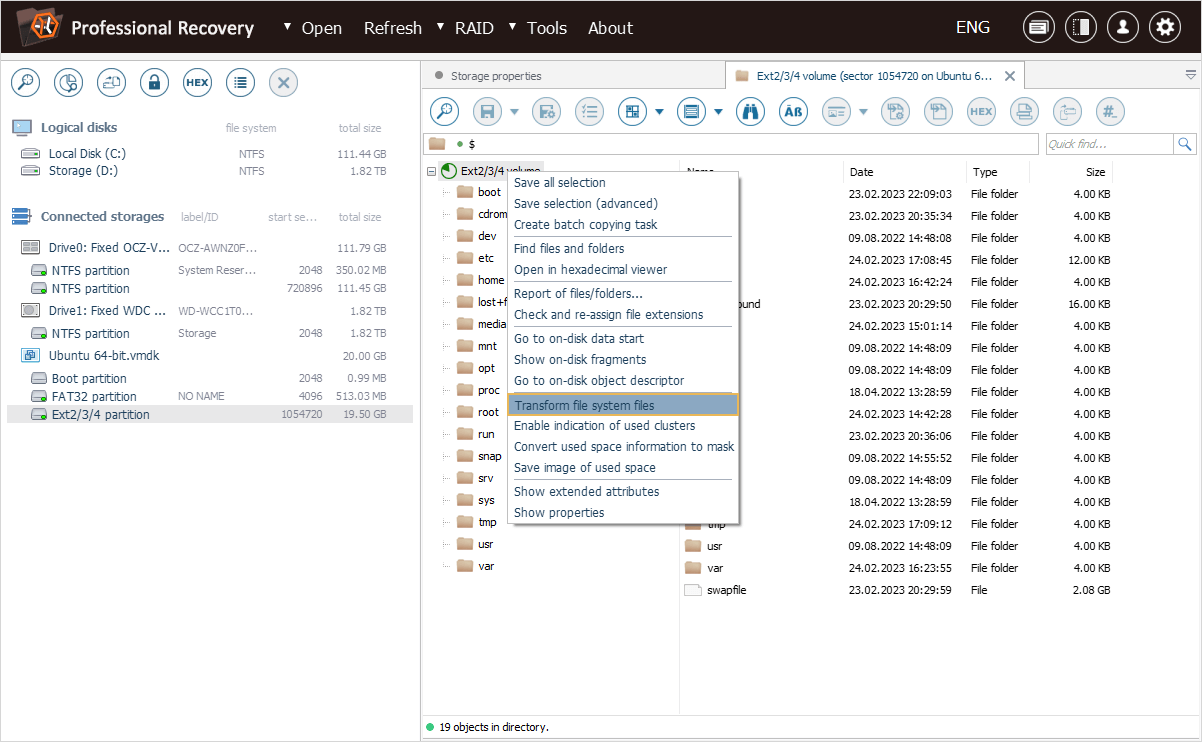
Now we can proceed to the "Transform file system files" option, presented in the context menu of our file system object.
In the opened dialog, we paste the copied random encryption key into the "Decryption password" field and change the "File names key length" property to 128 bits.
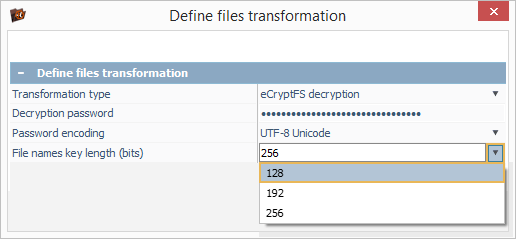
Yet, please mind that a specific instance of eCryptfs doesn’t contain the key length information for file names decryption. If the wrong key length is chosen, file names won’t be properly decrypted, even with a valid user’s password. If this happens, try using other key length options.
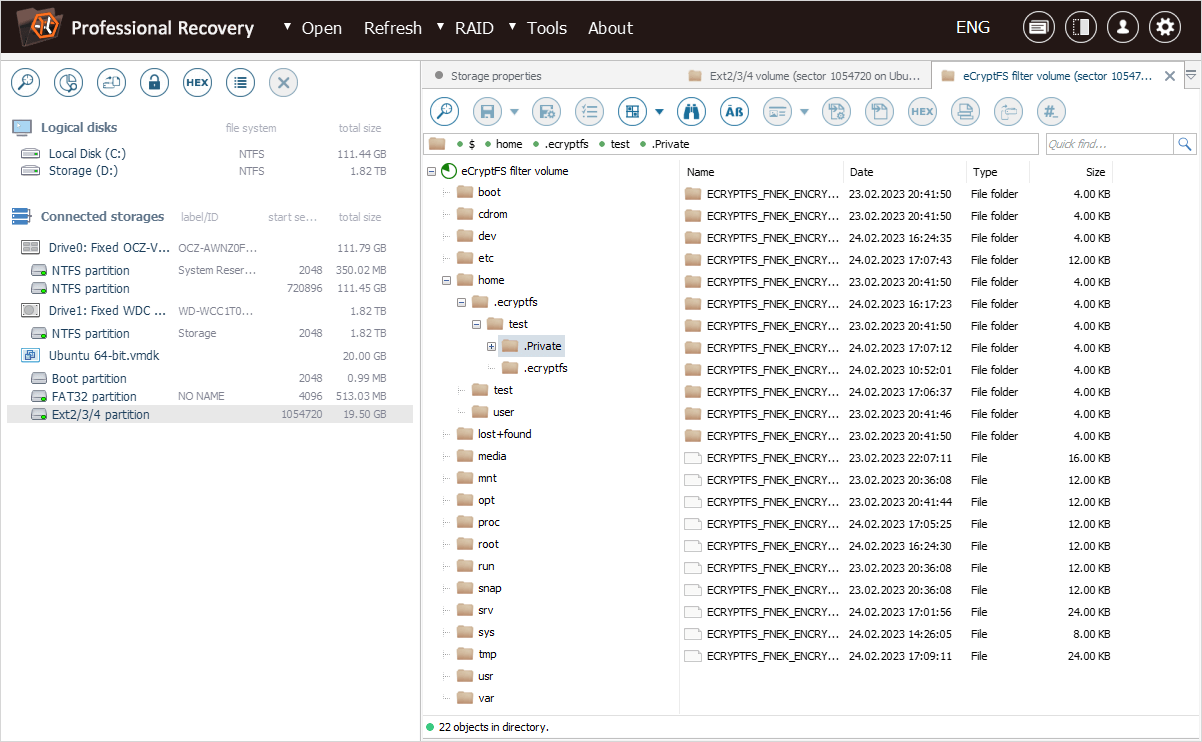
After we hit "OK", the software opens a new "eCryptfs filter volume", with the decrypted home folder of our "test" user.
eCryptfs recovery in a video guide
The following video will help you to get a more clear understanding of the eCryptfs decryption procedure:
Last update: August 18, 2023
