Unwrapping decryption keys in UFS Explorer for Linux eCryptfs or Synology Vault-based encryption
Designed to protect sensitive files, modern encryption systems like eCryptfs can pose serious challenges for data recovery or forensic analysis. One possible difficulty stems from the fact that the actual keys used to encrypt and decrypt folders or files are not stored on disk in plain form. Instead, they may be secured with an additional encryption layer known as "password wrapping". In such cases, the encrypted content may remain inaccessible, even when the physical storage is intact and a valid user password has been supplied, unless the encoded key is successfully "unwrapped". With a deep understanding of the major wrapping schemes, UFS Explorer is able to process and interpret wrapped key files, such as those generated by Linux eCryptfs or Synology's Vault-based LUKS encryption. By revealing the original encryption keys, the software allows specialists to access encrypted data that would otherwise remain locked.
Password unwrapping in UFS Explorer
The practice of wrapping encryption keys is not uncommon in modern encryption technologies. For example, in case of default home folder encryption under Linux, the real encryption key is randomly generated by the system. This key is then wrapped (i.e., encrypted) using the user’s login password and stored in ciphered form in a dedicated key file, typically named "wrapped-passphrase", located under ~/.ecryptfs/. As a result, entering the user’s password alone is not enough to access the encrypted volume – a specific key unwrapping procedure is required to retrieve the actual decryption key.
In contrast, the simplified eCryptfs-based mechanism (utilized by Asustor NAS and older Synology models running DSM 7.1 and earlier) allows unlocking the encrypted shared folder using just the user's password. However, if the password is lost and the NAS is unbootable, the only viable option is to retrieve the password from a backup key file (e.g., *.key or keystore), again requiring an unwrapping procedure.
A similar proprietary mechanism is implemented in newer Synology NAS devices. Here, the contents of an encrypted volume are protected by LUKS, with a randomly generated AES encryption key. This key is then encrypted (wrapped) using a password defined by the user and stored inside a special Encryption Key Vault container, along with metadata required to unwrap it. The user may choose to export the encryption key in Base64 format as an *.rkey file, which can later be used for decryption. However, if the *.rkey file is missing and cannot be restored, the password alone is insufficient for data access – the wrapped key and Vault files must also be analyzed to retrieve the actual encryption key.
The Professional and Technician editions of UFS Explorer offer dedicated tools that enable data recovery specialists to extract usable encryption keys from wrapped key materials provided by Linux eCryptfs and Synology Vault-based LUKS encryption, making it easy to unlock the encrypted content for data recovery or forensic examination.
To perform key unwrapping, the following inputs are required:
For Linux /home directory encryption:
- The "wrapped-passphrase" file (usually located under ~/.ecryptfs/);
- The user’s password (login passphrase).
For Synology NAS with DSM 7.2+ (Vault-based LUKS encryption):
- The Vault configuration file (vault_passwd.info);
- The wrapped encryption key file (*.wkey);
- The password used when creating the encrypted volume.
For Asustor NAS and legacy Synology (eCryptfs-based encryption):
- The backup key file (*.key or keystore).
This functionality is available in UFS Explorer via the "Password unwrap tools" option found in the "Tools" menu.
In the opened window, the user is presented with a list of unwrapping utilities. Selecting the relevant option opens a dialog tailored to the given encryption type.
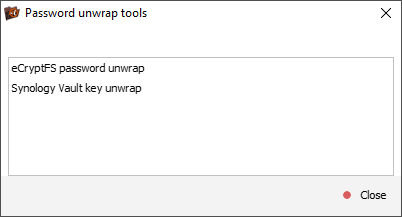
For eCryptfs, the user needs to provide the path to the wrapped key file, select the appropriate password encoding, enter the wrapping password and then click "Unwrap" to reveal the actual encryption key.
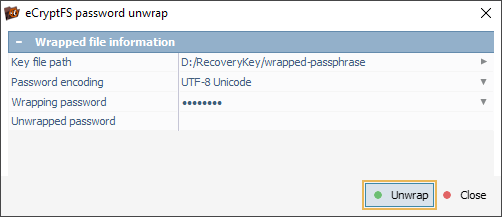
In case of a simplified eCryptfs implementation on NAS, the default wrapping password can be selected from the drop-down list.
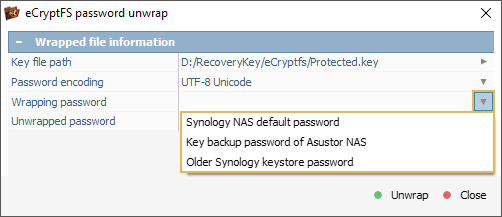
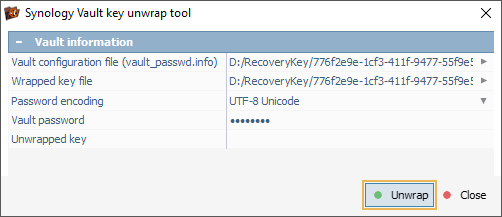
For Synology Vault, the user must load the Vault configuration and wrapped key files, select the necessary password encoding, enter the vault password and press the "Unwrap" button to extract the decryption key.
Decrypting encrypted Linux home folder
The following example demonstrates how UFS Explorer’s key unwrapping feature can be applied to recover an encrypted home directory on a Linux system.
In this case, the client lost access to their Ubuntu installation following a sudden power failure. The incident left some important documents trapped within the /home directory, which was encrypted by default using eCryptfs. The client agreed to provide the correct password for their system account.
Our technician creates a disk image of the drive removed from the client’s computer and opens it in UFS Explorer for further analysis.
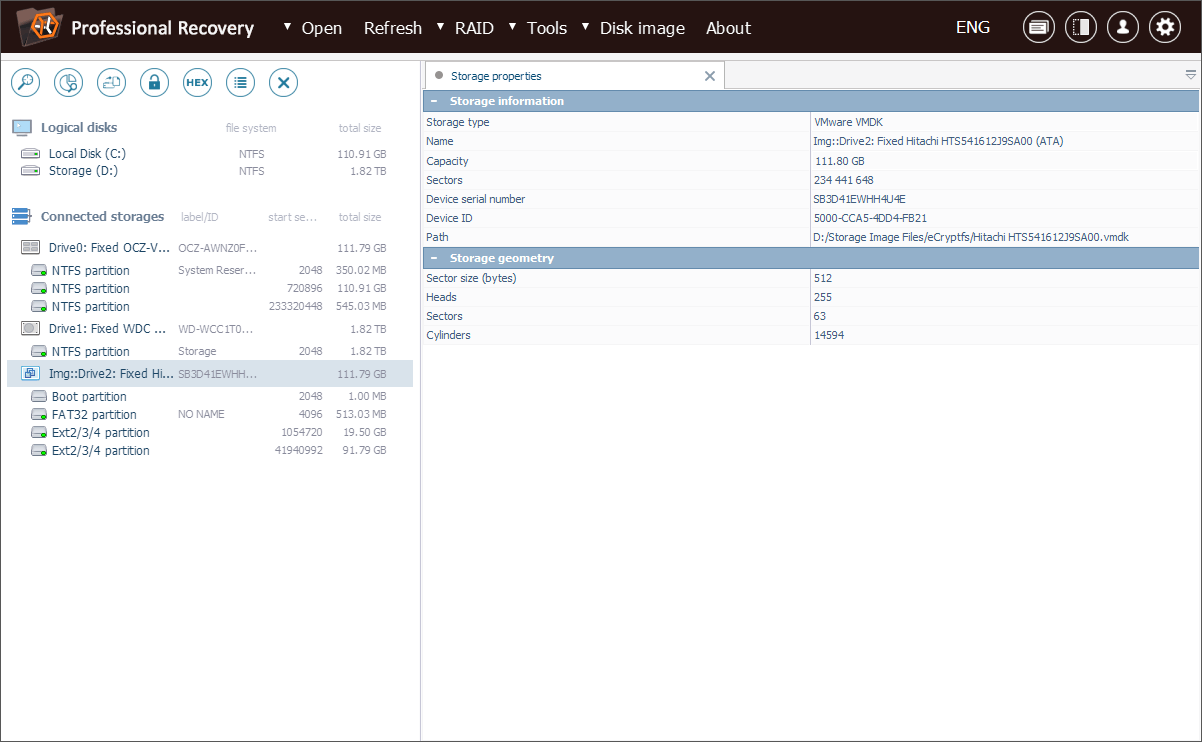
The encrypted data resides within the .ecryptfs folder, specifically within the .Private subfolder of the user’s home directory (in our example, the user is named "test").
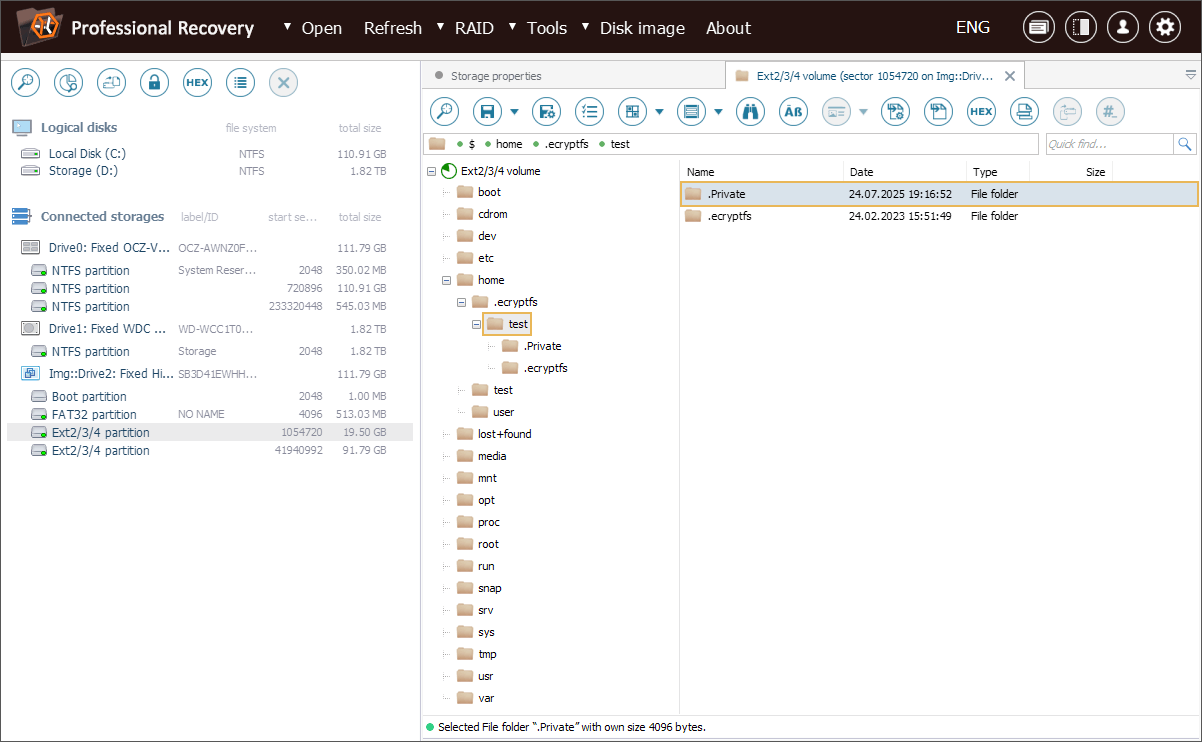
Inside .ecryptfs, there is a crucial file named "wrapped-passphrase", which contains the user’s actual encryption key, but wrapped (encrypted) with their login password.
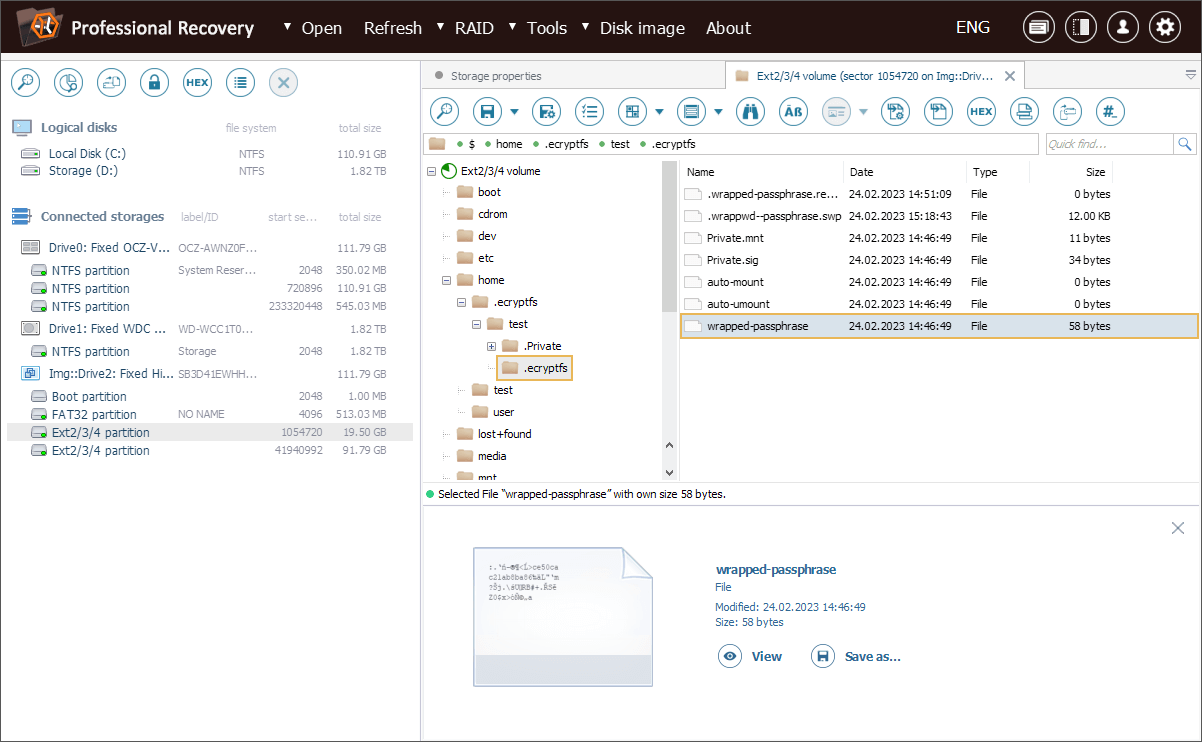
This "wrapped-passphrase" file must be copied to a secure location for further retrieval of the original encryption key.
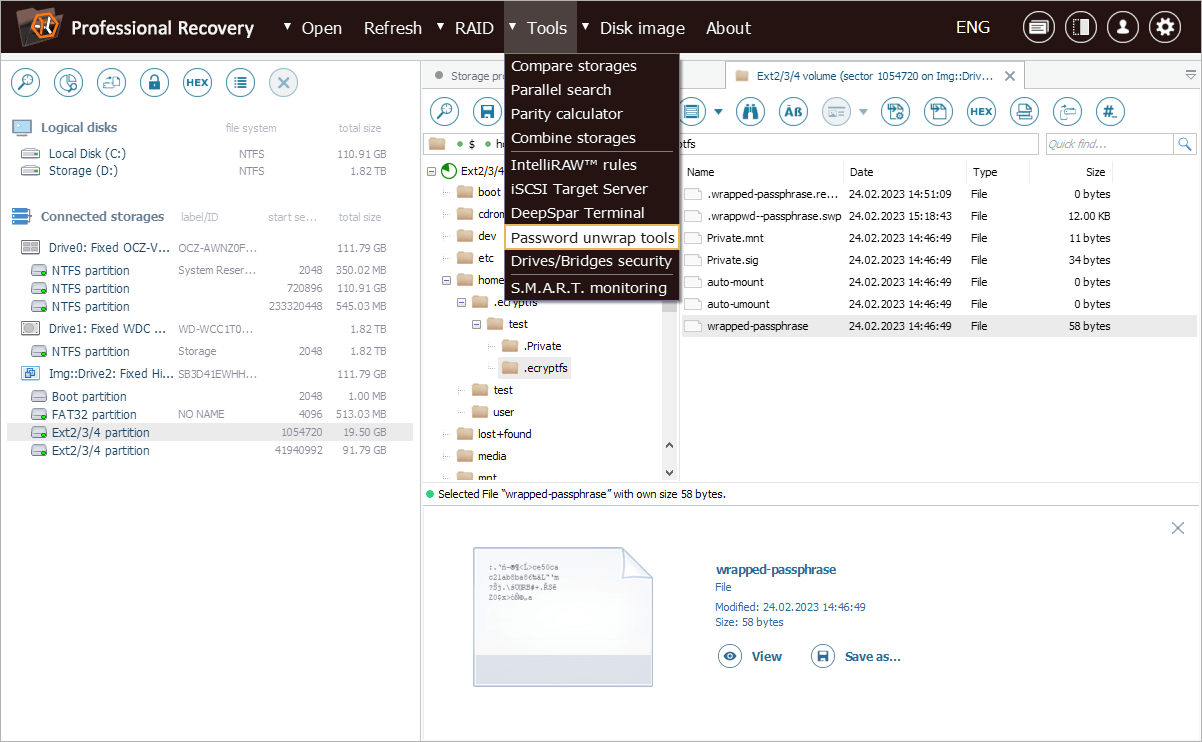
After that, we can select the "Password unwrap tools" option from the "Tools" menu and choose the "eCryptfs password unwrap" option.
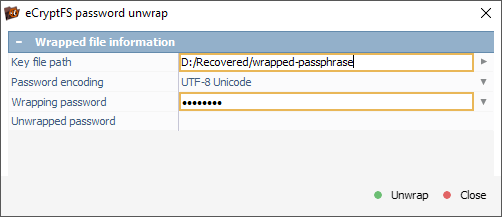
In the dialog that opens, we load the wrapped-passphrase file via the "Key file path" field and specify the user’s login password as the "Wrapping password".
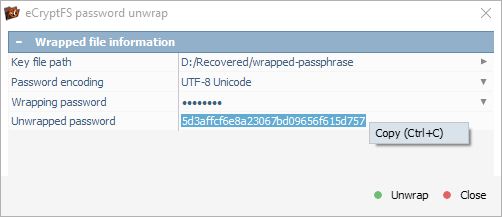
Once we press the "Unwrap" button, the decryption key shows up and can be copied to the clipboard.
Now we can follow the standard eCryptfs decryption procedure using the "Transform file system files" from the context menu of the encrypted file system object.
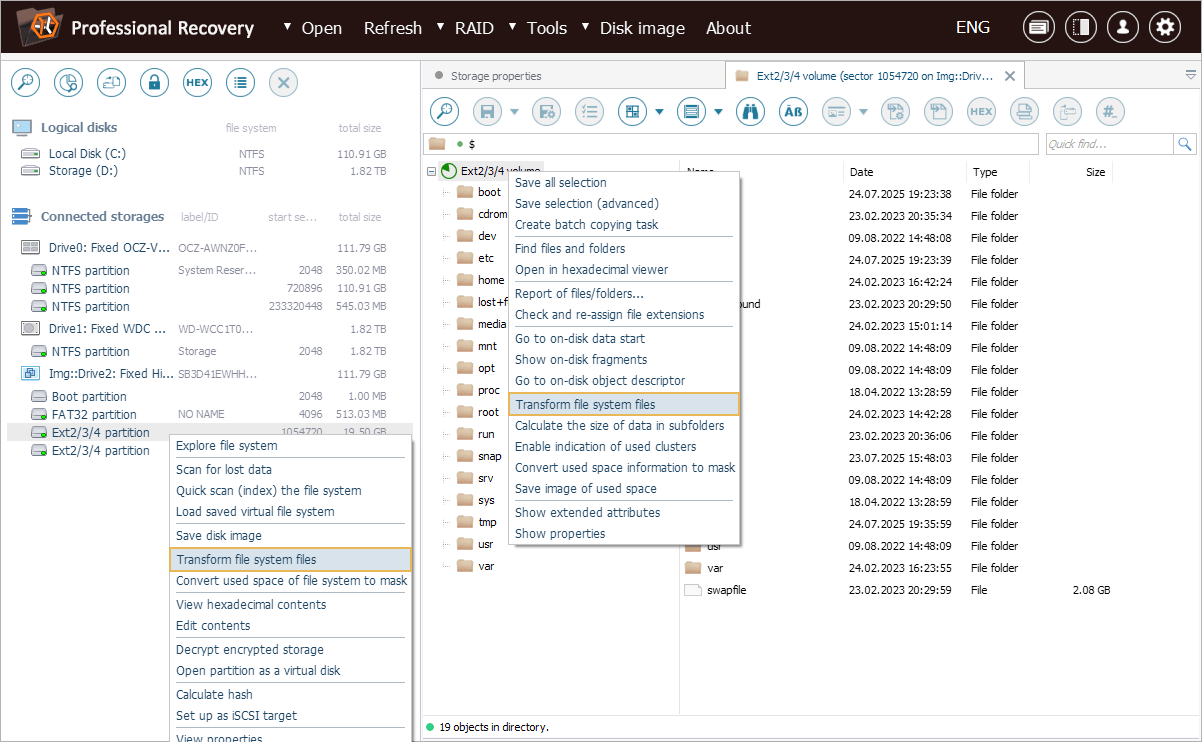
In the dialog that opens, we paste the deciphered key into the "Decryption password" field and set the "File names key length" to 128 bits, matching the encryption parameters used by eCryptfs.
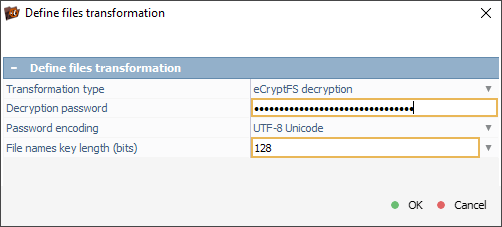
After confirmation, UFS Explorer creates a new "eCryptfs filter volume" tab, granting access to the decrypted contents of the client’s home folder, allowing us to begin recovering the important documents.
Unlocking Synology NAS encrypted with Vault-based LUKS
Another practical example involves a modern Synology NAS device with a Vault-based LUKS configuration.
A client had been using Synology DS3622xs NAS running DSM 7.2, with enabled volume encryption. The NAS experienced a hardware failure, rendering the storage inaccessible. However, the hard drives themselves remained undamaged. The client remembers the encryption password but does not have the exported *.rkey file, which could simplify the decryption process.
Our technician begins by creating disk images of the NAS drives and opens them in UFS Explorer. These images are used to reconstruct the storage layout and gather the files required for key unwrapping.
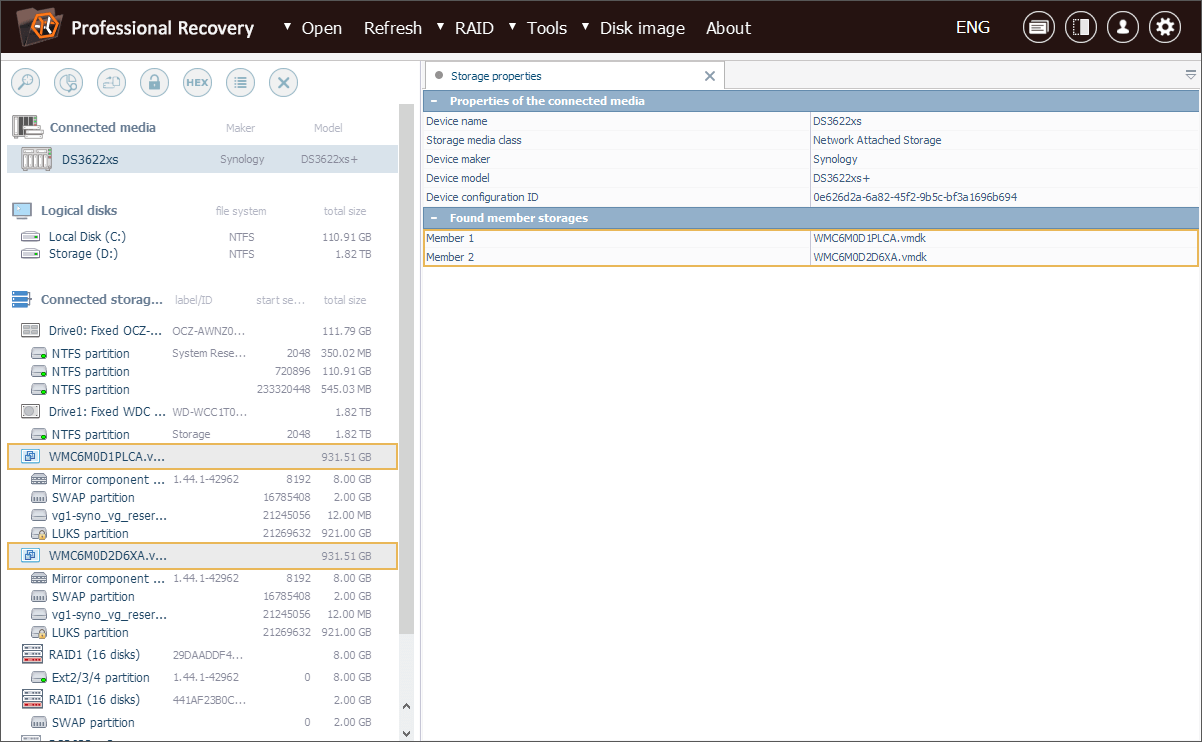
First, we locate the Vault configuration file named vault_passwd.info, found on the system partition under the path: /usr/syno/etc/encvol/<vault_UUID>/.
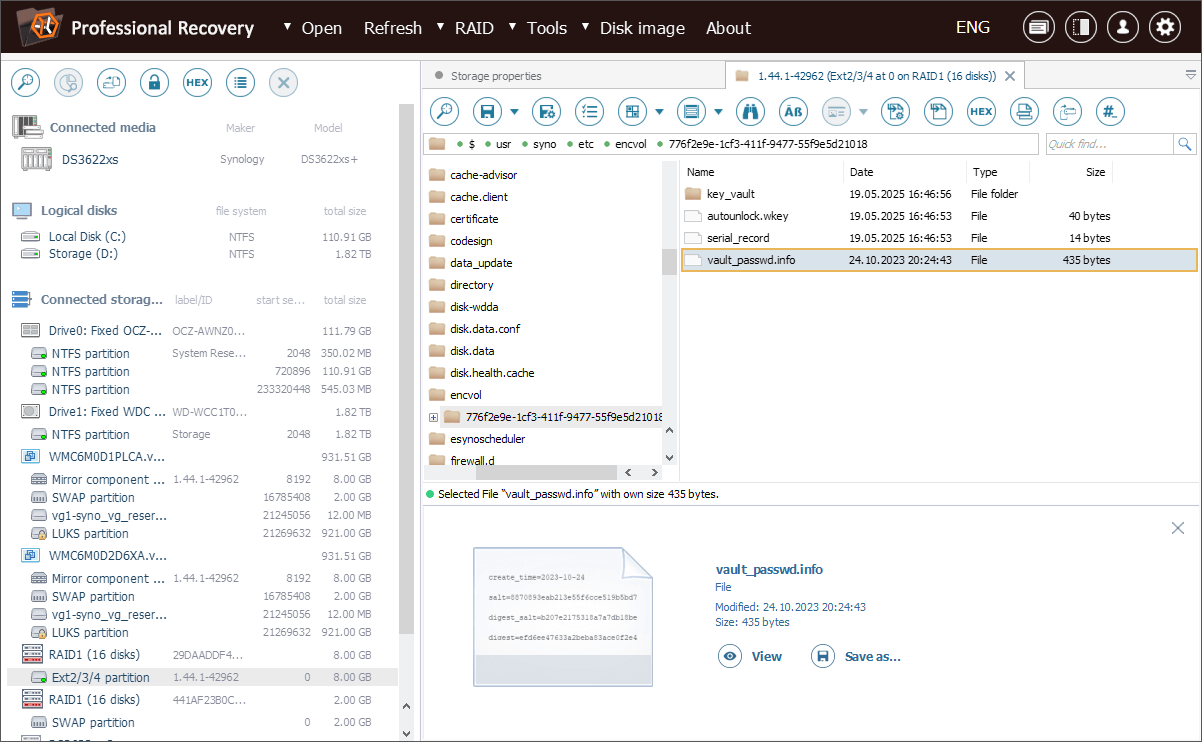
Next, we look for the wrapped key file with a *.wkey extension. It follows the <volume>_vp.wkey naming format and is stored inside: /usr/syno/etc/encvol/<vault_UUID>/key_vault/.
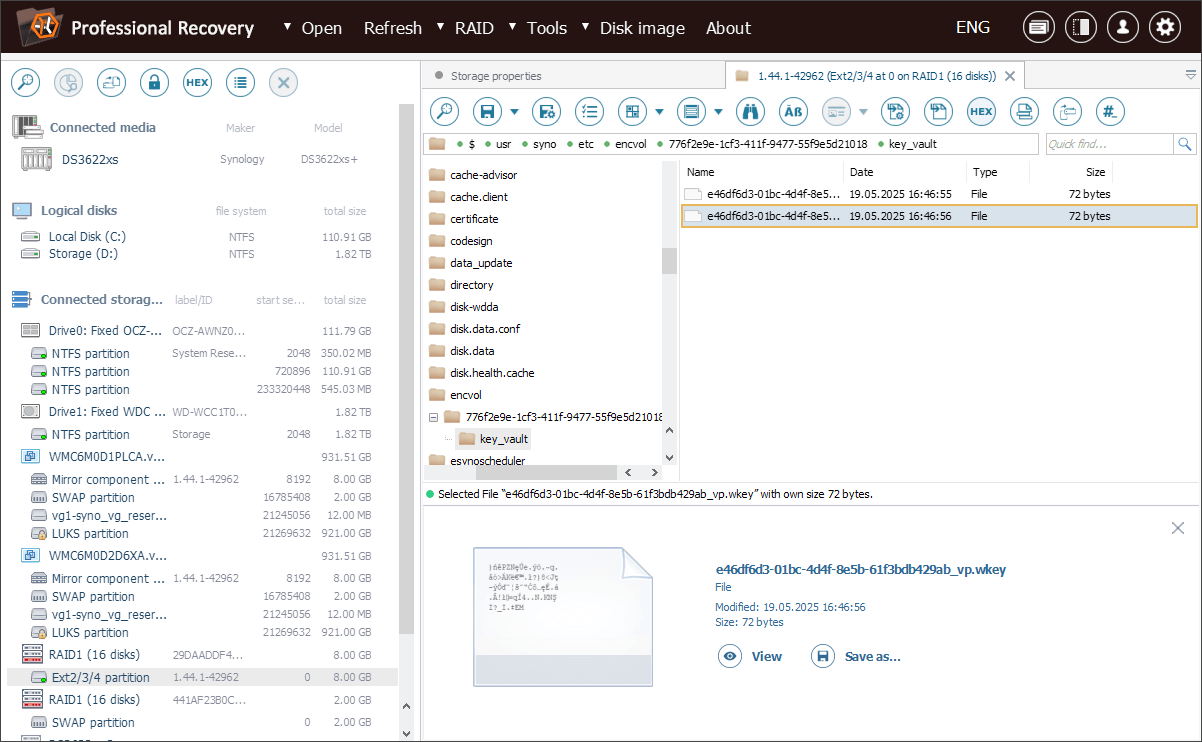
For convenience, we save the entire <vault_UUID> directory.
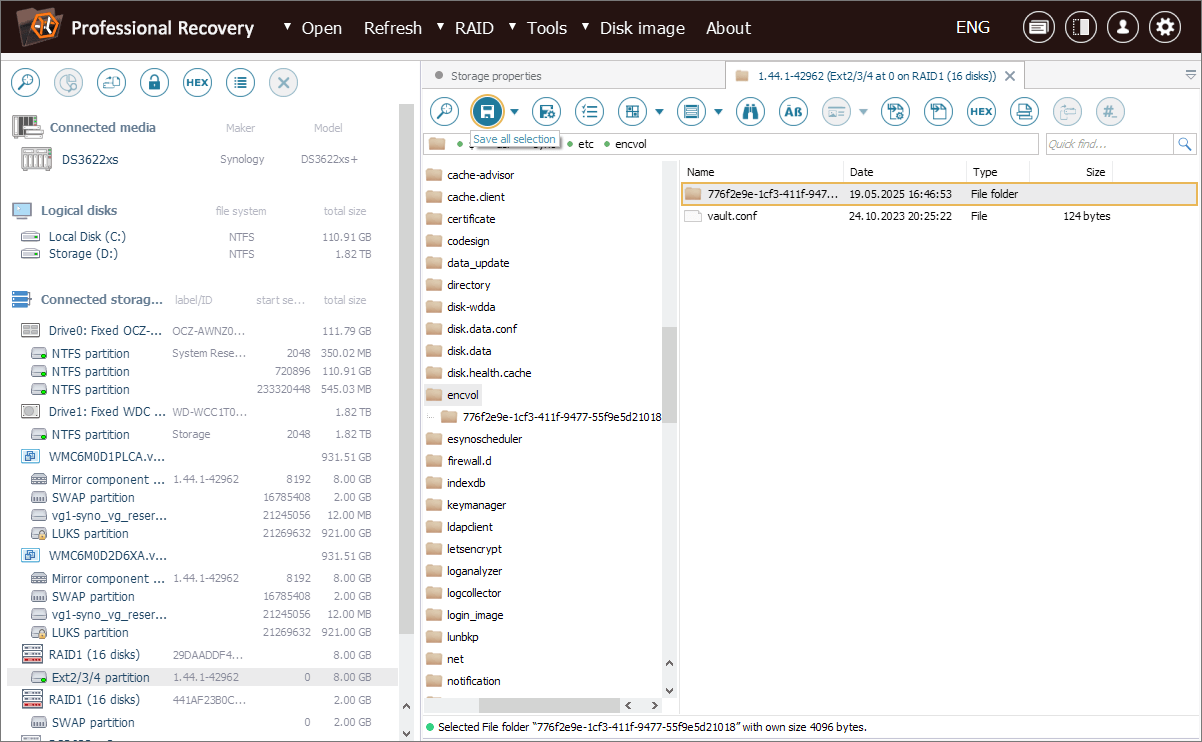
Now we can proceed to the "Password unwrap tools" option available in the "Tools" menu of UFS Explorer.
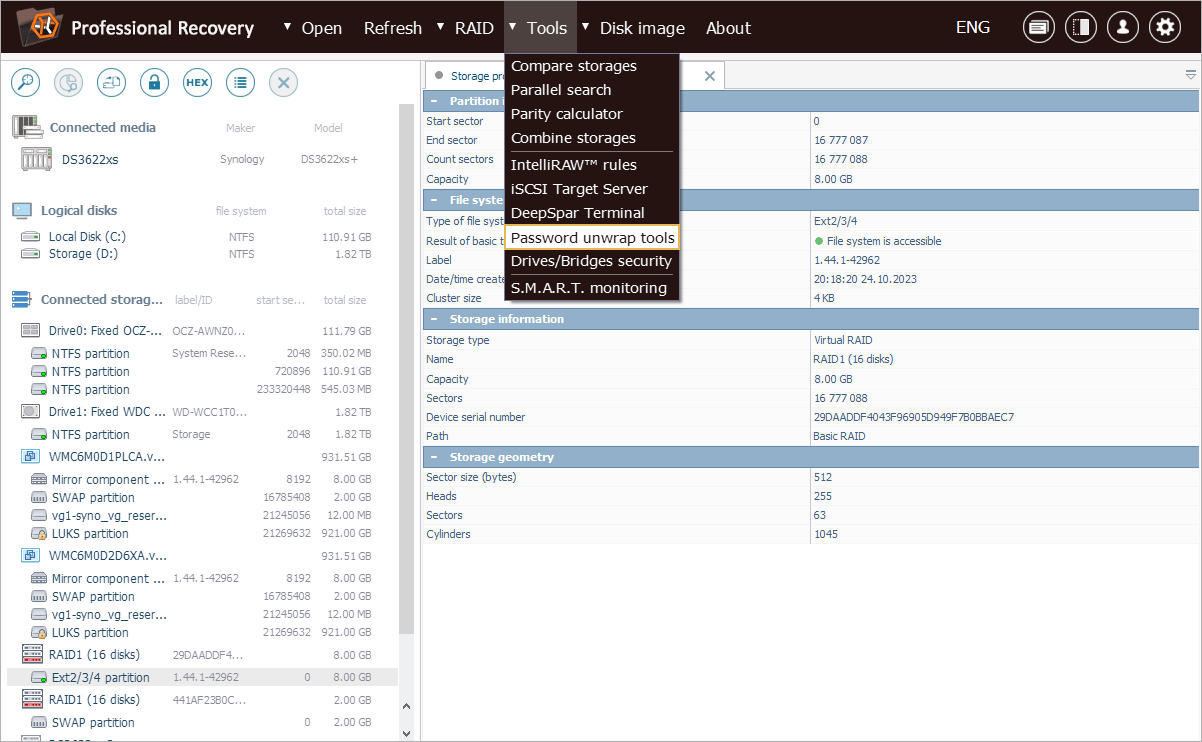
In the dialog that opens, we choose "Synology Vault key unwrap".
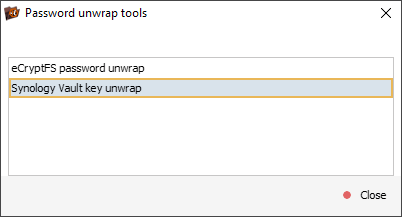
We provide the paths to both the Vault configuration file and the wrapped key file, then enter the password set by the user for volume encryption into the "Vault password" field.
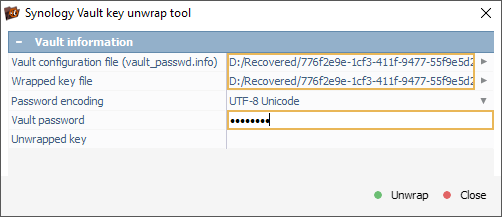
Once we click "Unwrap", UFS Explorer extracts the volume decryption key. This key is equivalent to the one stored in an *.rkey file, but is presented in hexadecimal format instead of Base64.
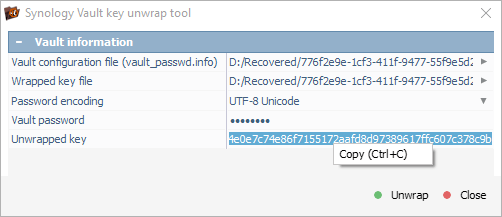
After copying the hexadecimal key, we open UFS Explorer’s tool for LUKS decryption.
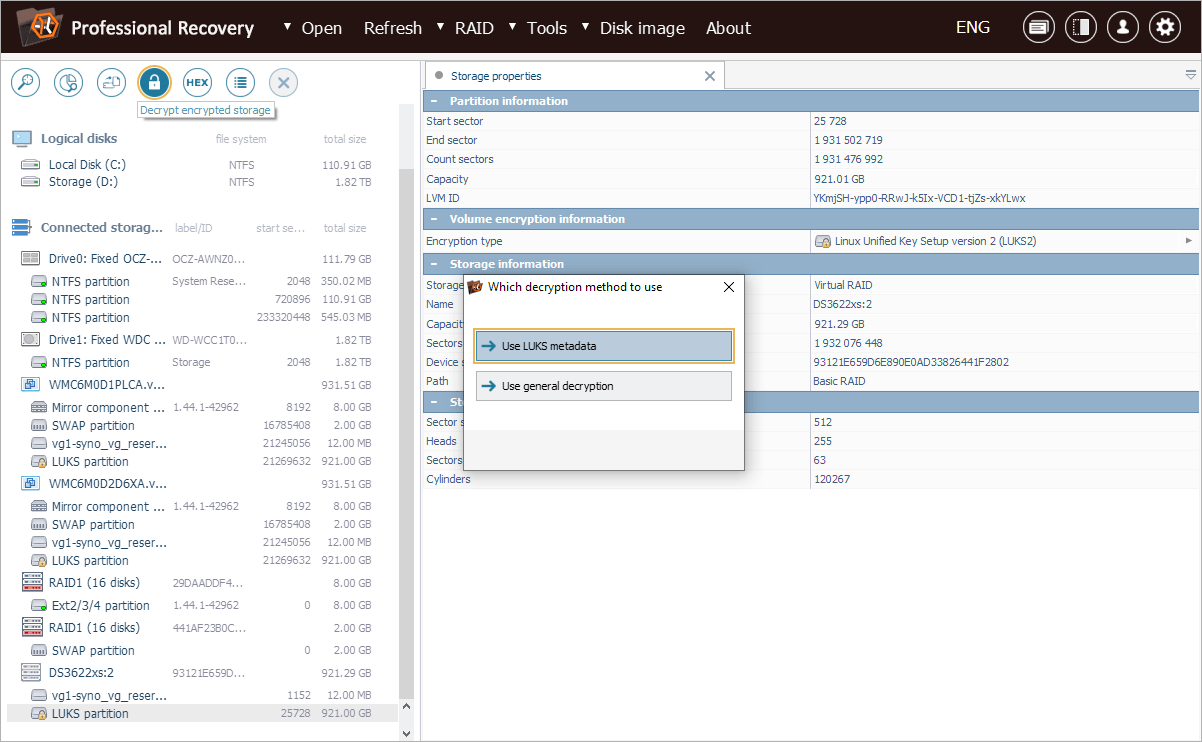
Here, we paste the obtained key into the "Password" field and ensure that "Password transform" is set to "Decode Hexadecimal" so the software can interpret it correctly.
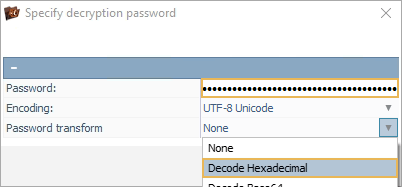
With the decrypted key in place, the encrypted volume is successfully unlocked, enabling us to recover the client’s data.
Last update: August 06, 2025
