Applying "file system files" transformations in UFS Explorer
As practice shows, not all storage systems follow conventional, straightforward patterns for organizing files within the file system. For example, many NAS devices use specialized data layouts, often relying on custom indexing structures, such as those based on internal "cloud" databases. To present their files in a usable form, additional processing is usually required, with the application of specific metadata or decryption credentials. Normally, the translations are performed in the background and do not impact end-users. At the same time, this storage logic may become a significant challenge during data recovery, since most standard recovery software lacks the ability to interpret those non-standard formats.
File system transformation in UFS Explorer
Without correct post-processing, the files in such file systems may be missing their original paths and names, or worse, remain completely inaccessible, even when the volume itself is readable. UFS Explorer of the Professional and Technician editions addresses this issue through file-system level transformations. During such transformations, the software interprets the content using the rules specific to the respective storage format, ensuring that users can recover the original files and directories, rather than meaningless or ciphered items.
The transformation functionality can be activated via the "Transform file system files" option in the partition’s context menu or the same option available in the context menu of a file system object within the Explorer (file browser) interface.
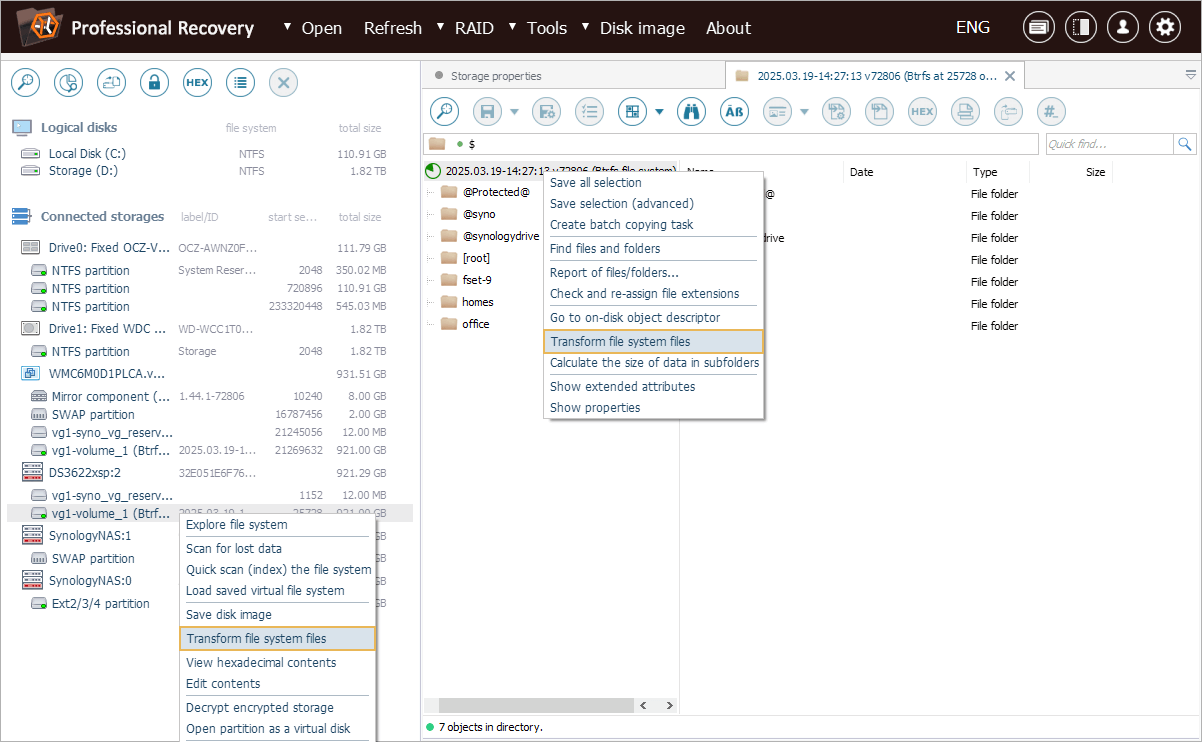
The currently supported layouts include WD My Cloud, Synology SynoDrive, Promise Apollo and eCryptfs, and this list is expected to grow in the future.
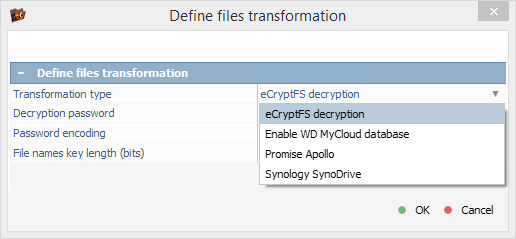
The software may detect the appropriate metadata automatically and suggest the necessary transformation type, which the user can then apply with a single click.
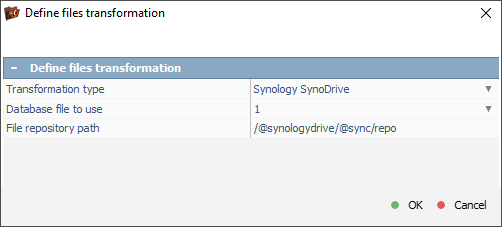
In cases when the associated metadata is not detected, users can specify the location of the relevant file repository folder manually.
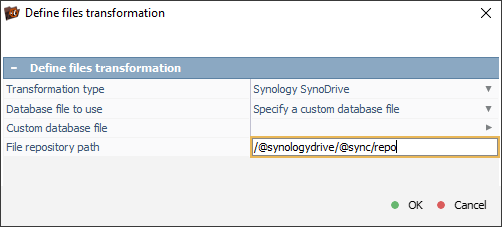
Additionally, it’s possible to provide a custom cloud database file containing the format-specific metadata required for the transformation.
Processing WD My Cloud Home volumes
Let’s consider an example case illustrating the usefulness of this feature in a real data recovery scenario. Our client needs to recover some valuable photos from a WD My Cloud Home device. The NAS is no longer accessible over the network, but the SATA drive extracted from it is perfectly intact. Our technician has connected this drive to the computer and created its image for further data recovery in UFS Explorer.
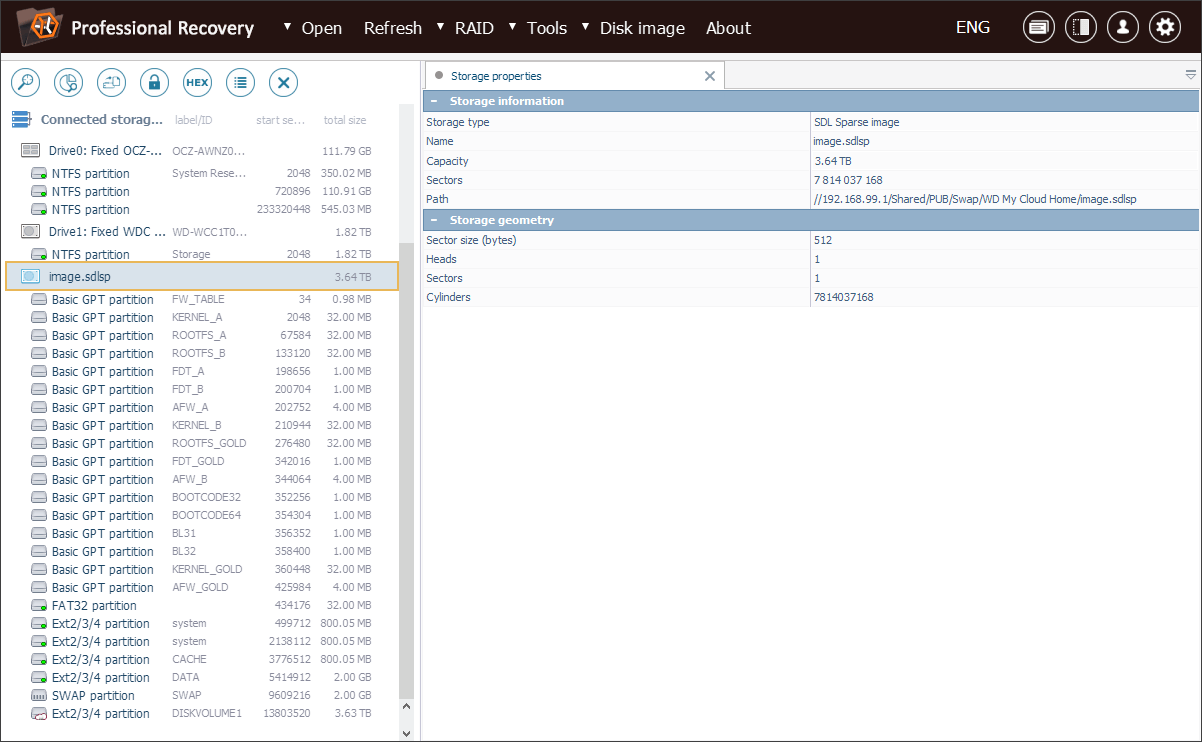
We see that the drive contains numerous service partitions. Among them, we locate the largest Ext-based partition labeled with a "cloud" icon – this is the one that holds the user’s files. The partition is accessible, therefore, we can open its content in Explorer (file browser) right away.
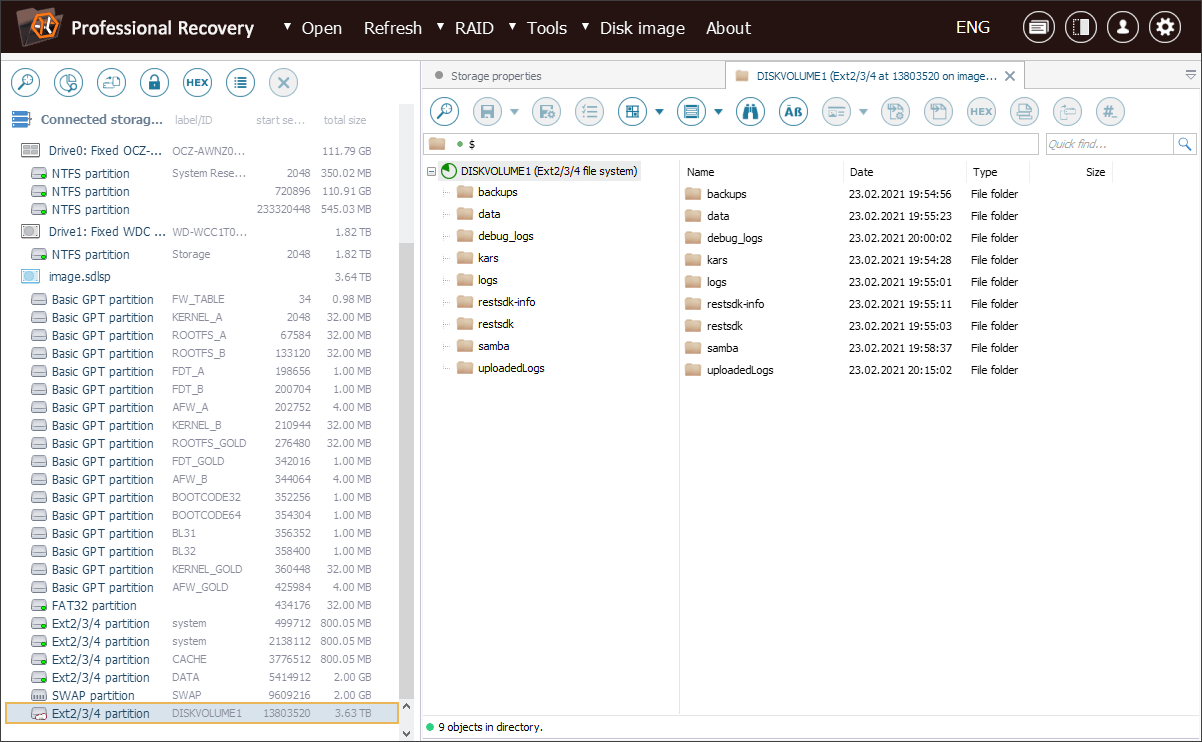
Yet, all the files there appear with random alphanumeric names, with no recognizable folder structure. Consequently, it is impossible to identify the necessary photos.
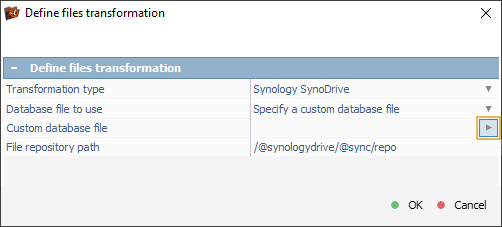
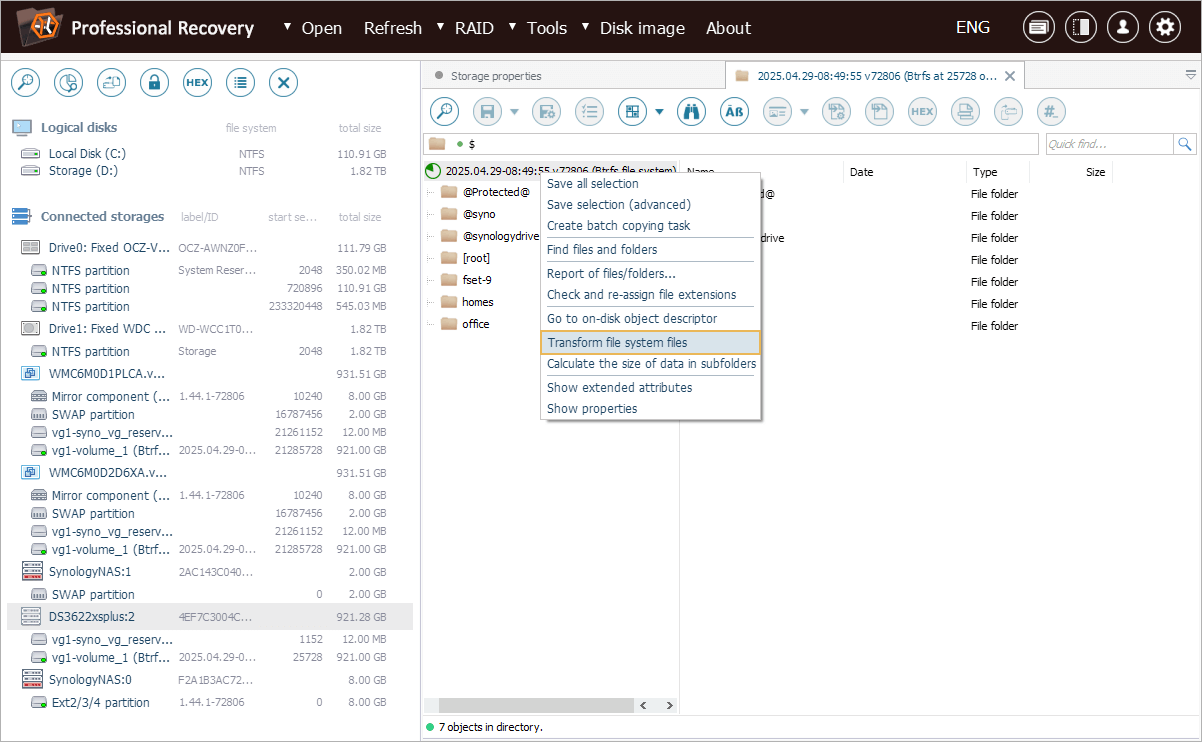
To restore the original layout, we need to open the context menu of this file system object and select the "Transform file system files" option from it.
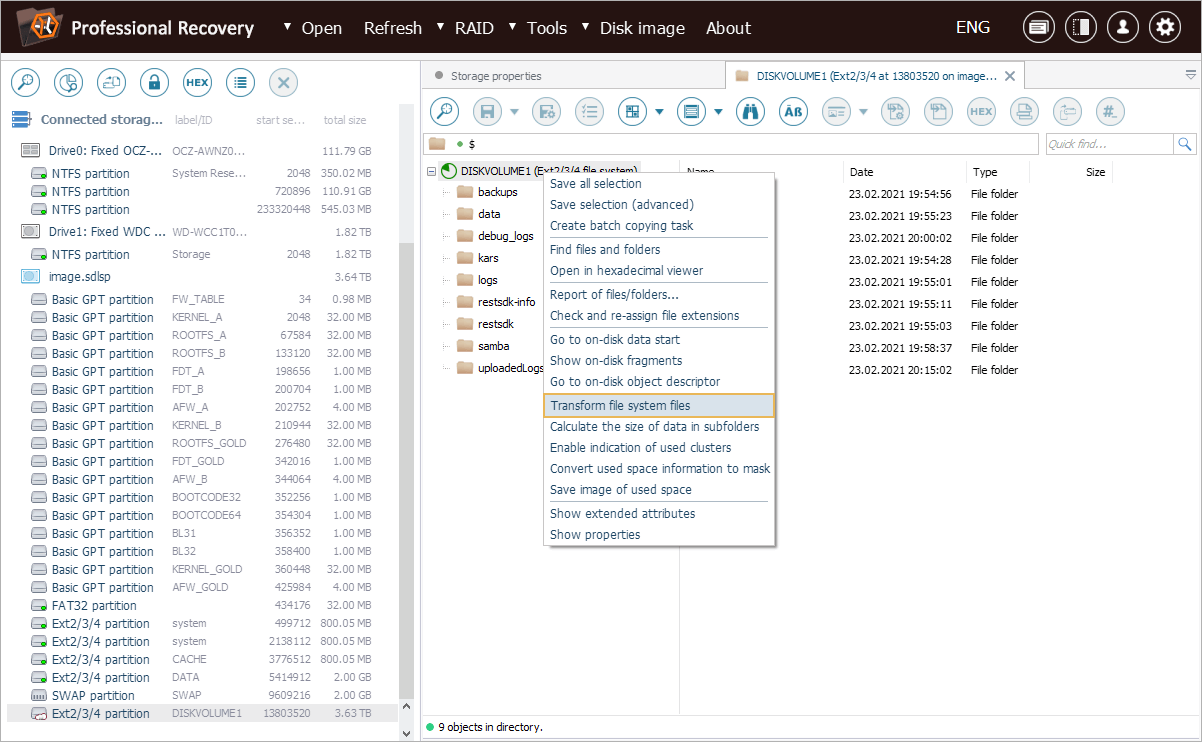
The software recognizes the WD My Cloud format and suggests the appropriate transformation type, using the WD My Cloud database.
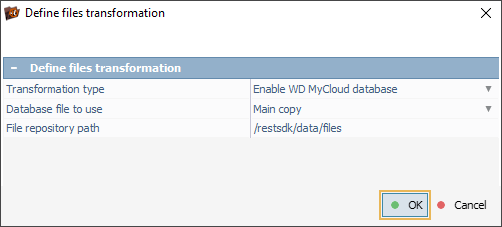
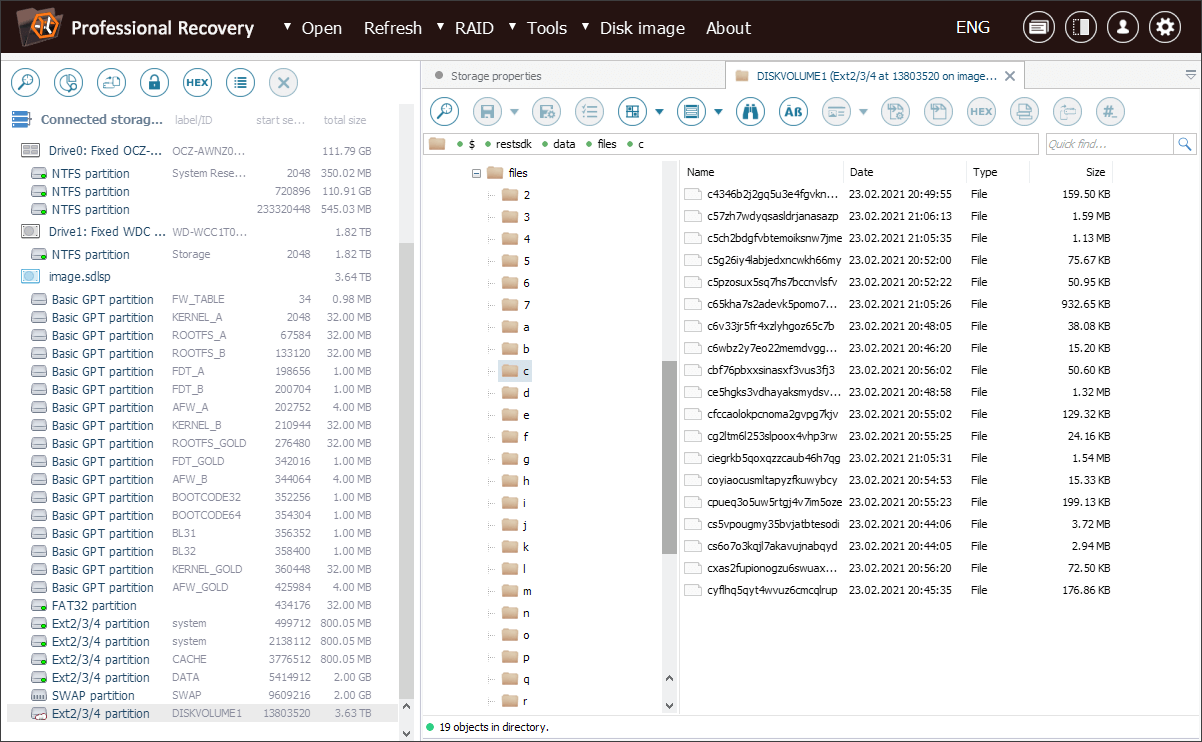
After we click OK, the program finds the respective index database and transforms the file system. As a result, the folder hierarchy and file names are presented correctly in a new tab.
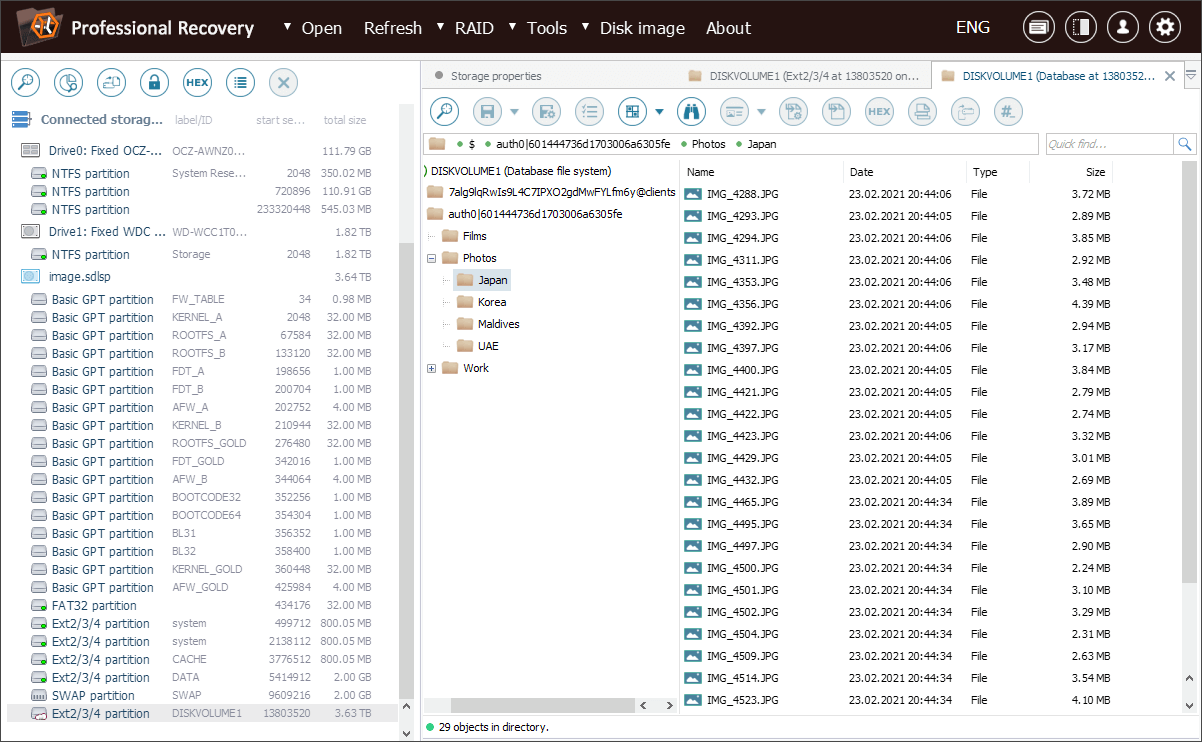
Now we can easily navigate the file system and copy the required photos.
Decrypting folders encrypted with eCryptfs
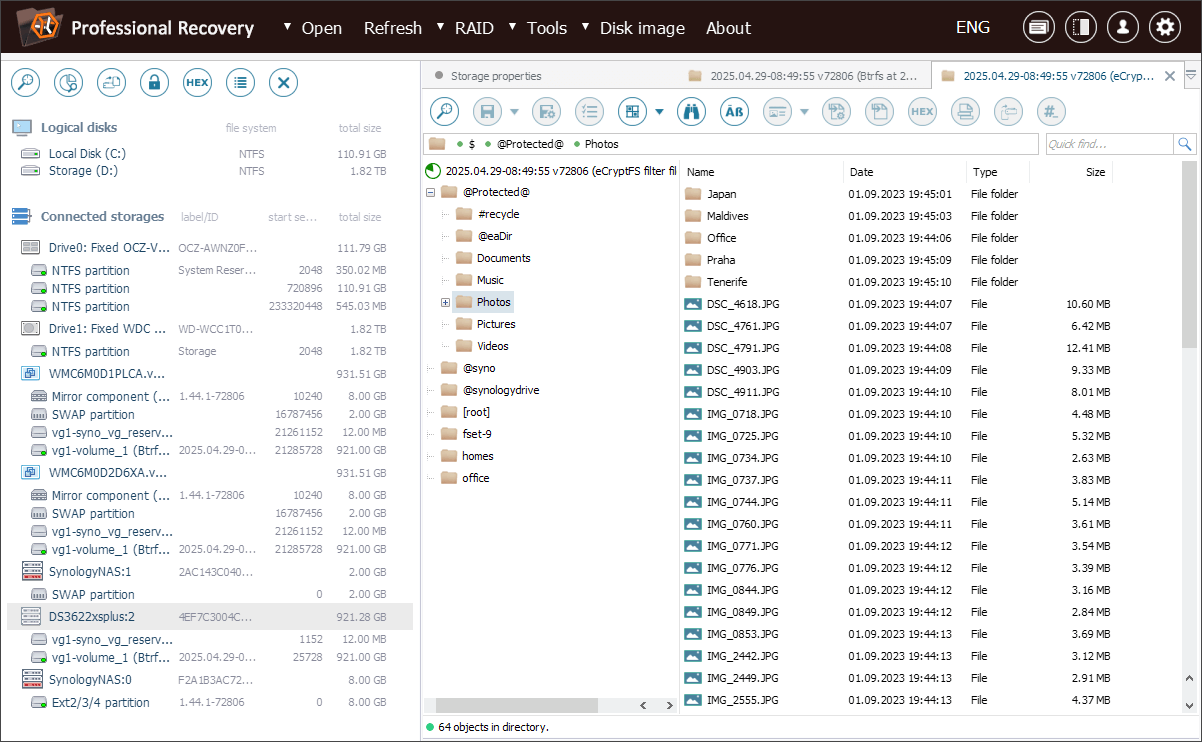
A slightly different example involves a device that employs eCryptfs encryption, such as a Synology DS3622xs+ NAS from another client. In this case, the storage fails to boot, but the client urgently needs to retrieve some important documents from an encrypted shared folder.
After completing the necessary preparations, we can locate the encrypted data – it is stored in a folder at the root of the Btrfs volume, named after the original client’s shared folder but enclosed in "@" symbols.
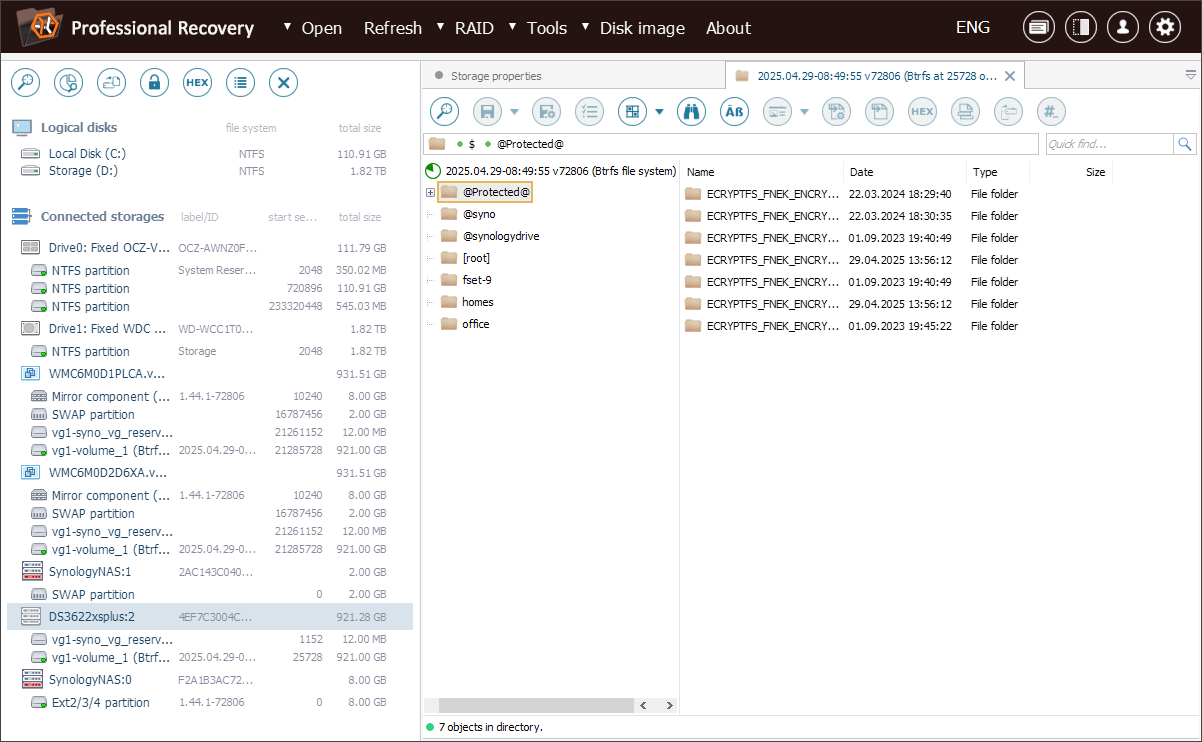
Inside this folder, all file names start with the prefix ECRYPTFS_FNEK_ECRYPTED., followed by a base64-encoded Encryption ID and a base64-encoded encrypted file name. The file contents are unreadable as well.
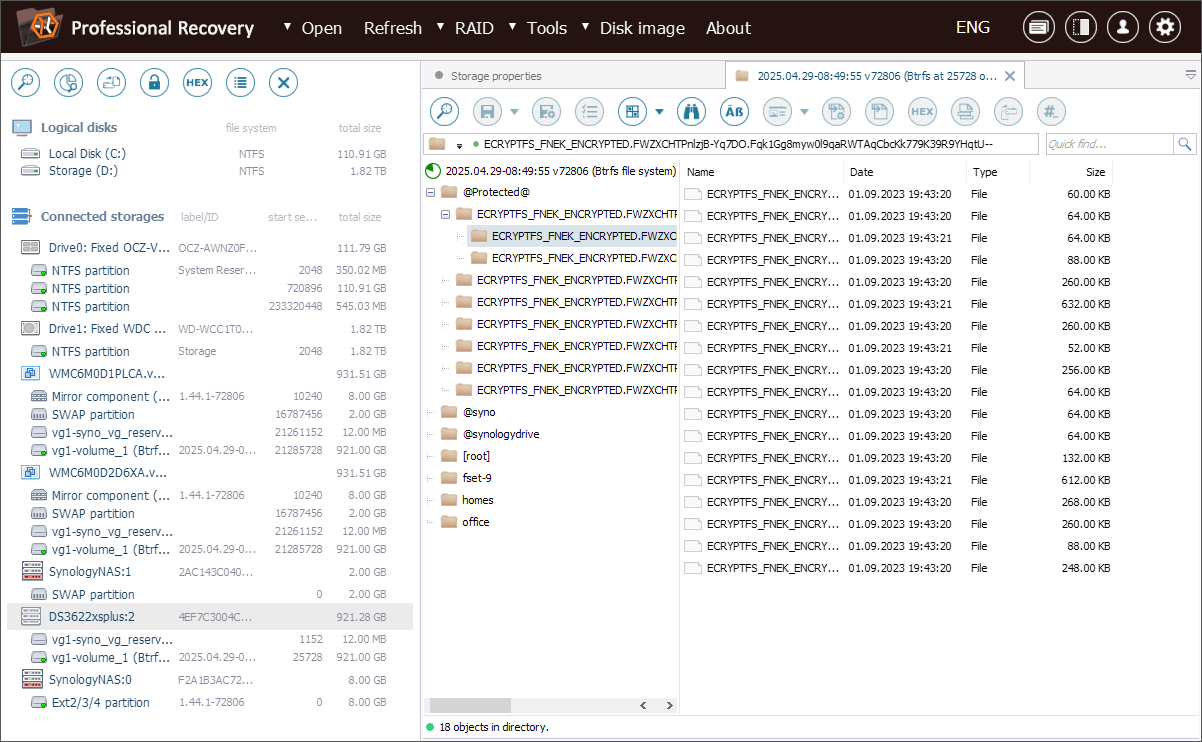
To decrypt the data, we right-click the file system object in Explorer (file browser) and choose the "Transform file system files" option from the context menu.
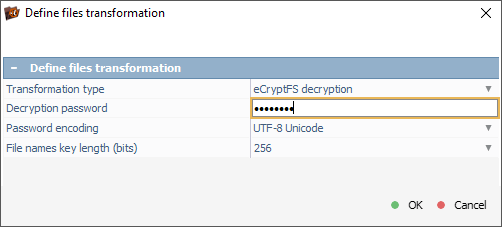
In the opened dialog, we need to select the eCryptfs transformation type and enter the encryption passphrase provided by the client into the "Decryption password" field.
Once we confirm the transformation, the software uses this passphrase to decode both the file names and content. The decrypted files are then displayed in a new tab, so we can easily browse and copy them, just like from a regular file system.
Last update: May 01, 2025
