Decrypting encrypted storages in UFS Explorer
Encryption has become a routine challenge in both data recovery and digital forensics, where specialists frequently encounter digital media protected by various cipher technologies. Although encryption does not necessarily prevent data recovery, it can introduce significant complexities into the process: encrypted data appears as unstructured noise, unless the correct credentials (such as a password or encryption key) are provided and properly applied to unlock the storage. Meanwhile, attempting to mount such a storage in its original environment may not only be troublesome under the given circumstances, but could also modify the original content, affecting the integrity of lost data.
In these situations, decryption is often delegated to data recovery software. However, the success of the procedure depends on several critical factors:
Encryption must not be enforced by hardware components (e.g., TPM chip, Apple Silicon);
The password or encryption key must be known;
The essential encryption metadata (headers, key containers, etc.) must be intact or reconstructible.
Each encryption system has its own architecture, defining how the keys are stored, how metadata is organized and how the decryption process should be performed. Therefore, data recovery software must explicitly support the specific encryption method in order to detect an encrypted volume, locate and interpret its metadata, apply the appropriate decryption mechanism and reconstruct the decrypted file system.
Basic data recovery tools usually support only a few popular encryption schemes, such as Windows BitLocker or Apple APFS, and are not equipped to handle less common formats like Linux LUKS or VeraCrypt. In contrast, the Professional and Technician editions of UFS Explorer offer extensive support for encrypted storage, with all decryption performed in a non-destructive, read-only manner. The software automatically detects compatible encryption technologies and labels them accordingly in the interface. Users can then enter the required credentials to unlock access directly in the program. If necessary, the software can also apply appropriate transformations to the password or key (e.g., for LUKS on Synology or QNAP NAS devices). Once decrypted, the file system becomes accessible for analysis and data recovery just like any regular partition.
The currently supported encryption schemes include:
Generic full-disk encryption
BitLocker (Windows)
FileVault 2 (macOS)
APFS encryption, FileVault (macOS)
LUKS1 and LUKS2 (Linux or customized implementations)
TrueCrypt and VeraCrypt (multi-platform)
Softraid with native encryption (OpenBSD)
GELI full-disk encryption (FreeBSD/legacy FreeNAS)
This functionality is presented in the interface as the "Decrypt encrypted storage" tool, accessible via the context menu of a selected drive or partition.
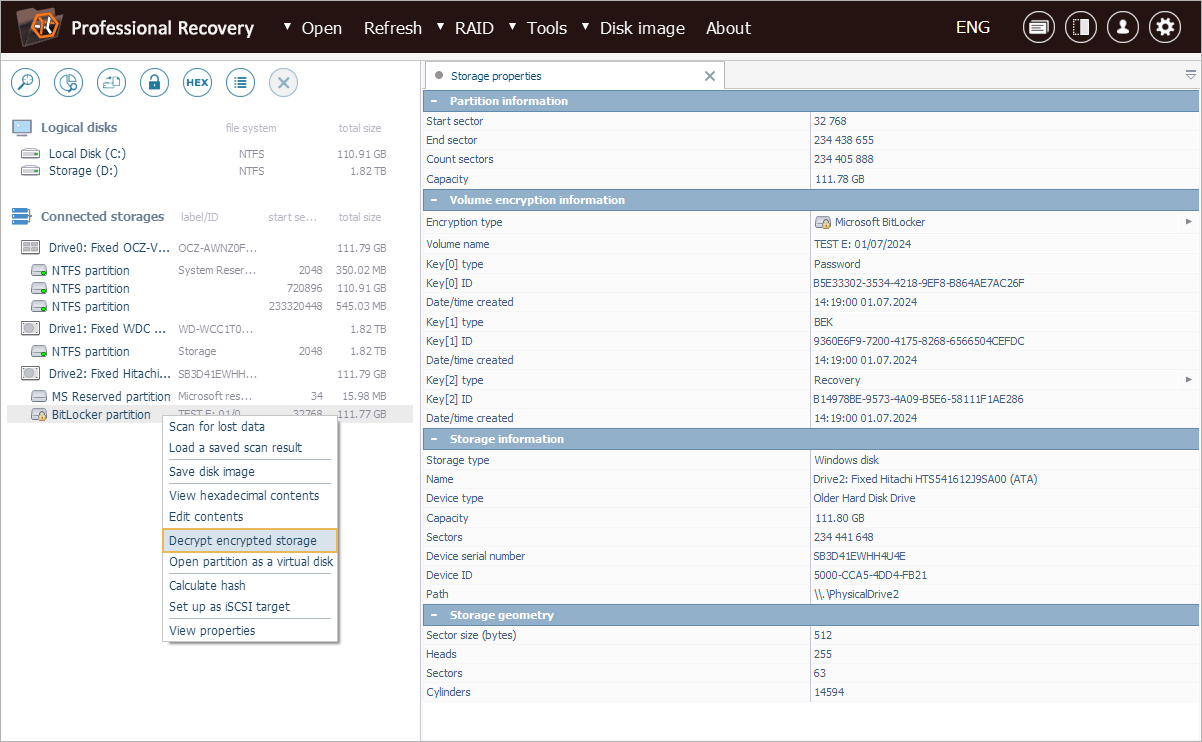
Alternatively, decryption can be initiated right away by clicking on the encryption indicator next to the storage in the list.
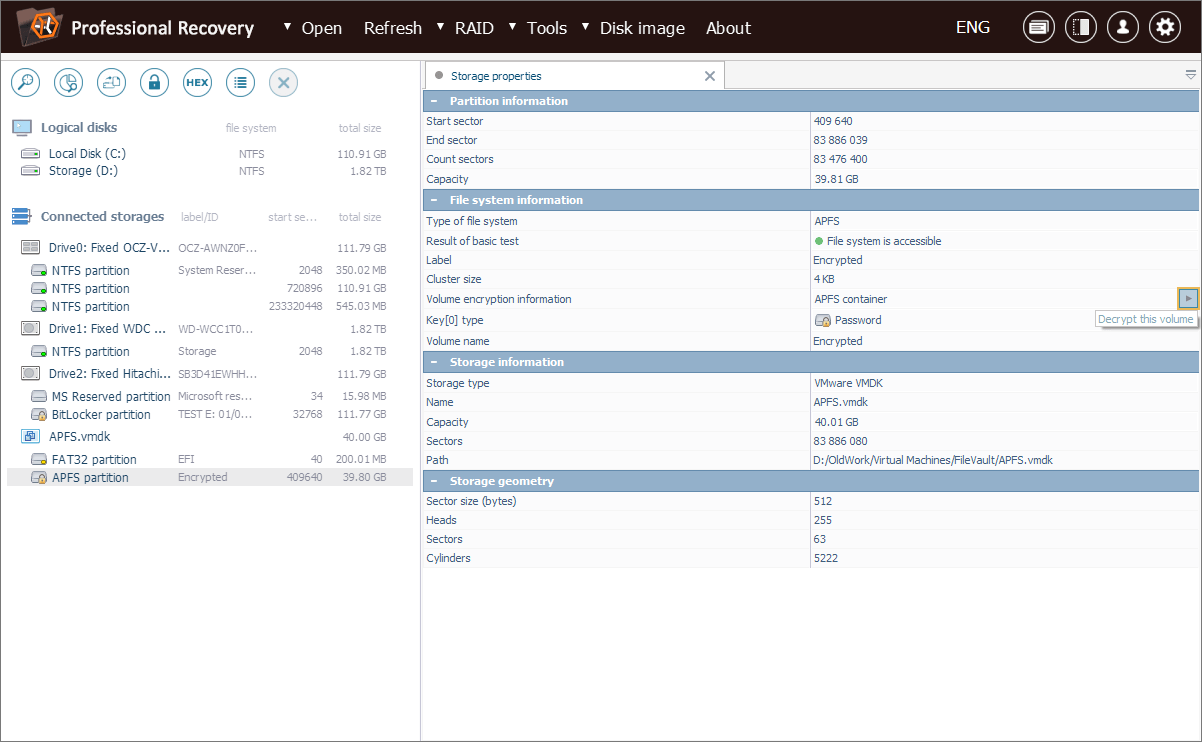
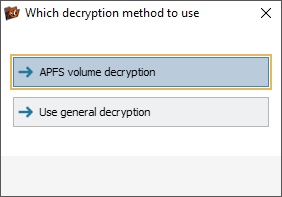
If the encryption technology is recognized by the software, it will prompt the user to apply the appropriate decryption method.
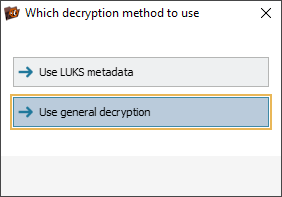
Otherwise, the user can proceed with the general decryption procedure.
The decryption dialog will be adjusted accordingly, based on the specific encryption technology involved. Depending on the scheme, it may include such parameters as a password or passphrase, applicable character encoding, a recovery key, transformation settings, the path to an external key file and other inputs specific to the selected encryption method.
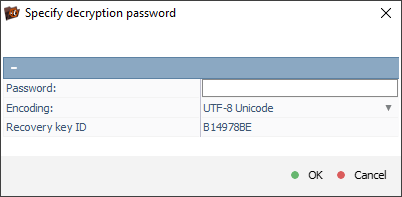
On the other hand, the general decryption dialog provides full control over the decryption process using advanced cryptographic parameters. These include the encryption algorithm (e.g., AES, Serpent, Twofish, Blowfish), the cipher block chaining mode (CBC, ECB, XTS), the initialization vector, key length (128, 192 or 256 bits), decryption block size (in bytes), and the actual cryptographic key required to unlock the data.
Now let’s look at a real-world example illustrating how this tool handles decryption in the case of a VeraCrypt-encrypted volume.
A client accidentally deleted several important work projects from an external hard drive. For confidentiality, the entire drive had been encrypted using VeraCrypt. The client knows the encryption password and provided it to our technician. No keyfile or PIM (Personal Iterations Multiplier) was used.
Before beginning the data recovery process, the encrypted layer needs to be properly decrypted. Obviously, we are not going to risk mounting the drive on a live system, as doing so might overwrite the deleted data. Instead, we connect the digital medium to our recovery workstation and run UFS Explorer.
The software detects the drive but displays it as having no valid partitions.
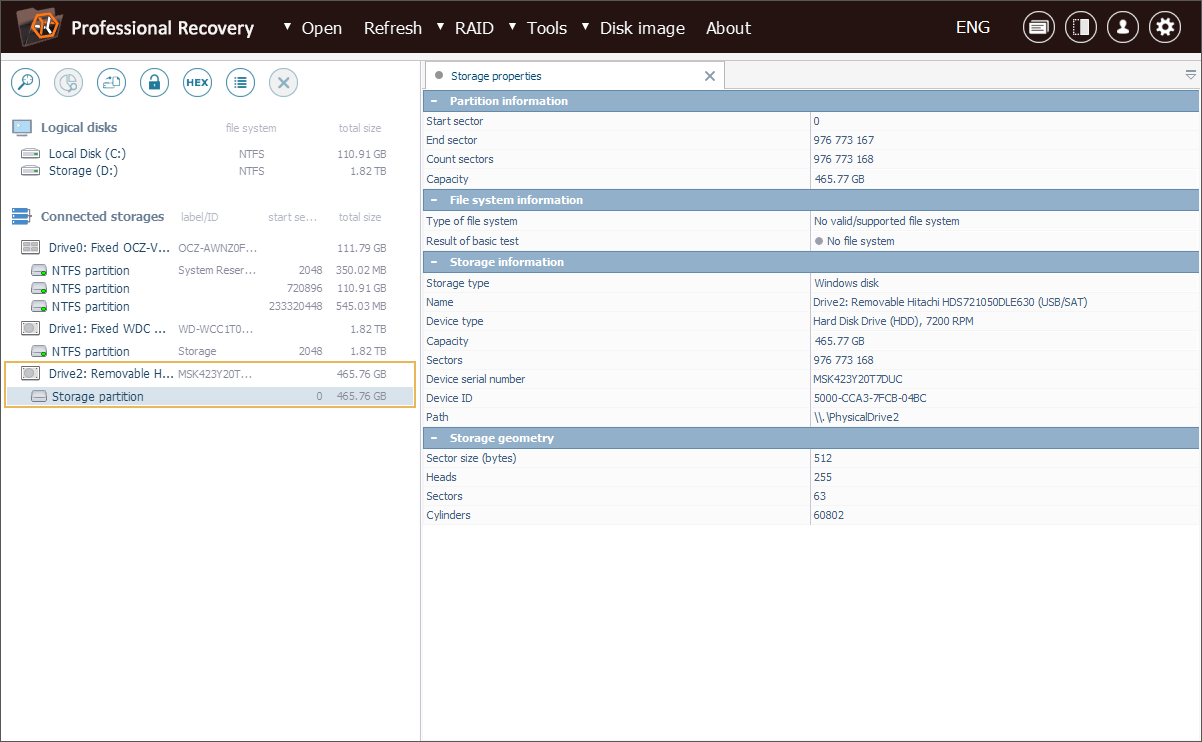
This is not an error, since, unlike BitLocker or LUKS, VeraCrypt volumes are intentionally designed to appear as random data, without identifiable metadata structures. This prevents such volumes from being auto-detected, which is a feature of the encryption solution itself.
Since the VeraCrypt volume is not recognized automatically, we select the supposedly encrypted partition manually and choose "Decrypt encrypted storage" from its context menu to open the decryption dialog.
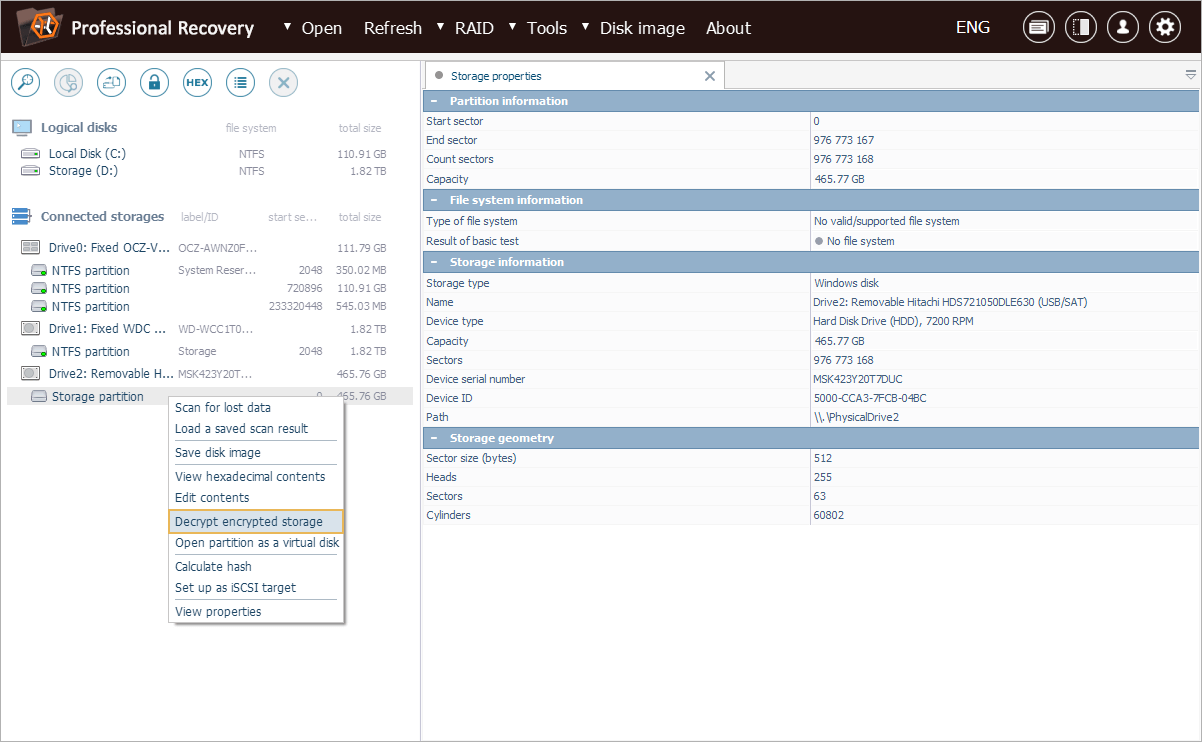
In the dialog, we switch to "TrueCrypt/VeraCrypt password decryption" mode, which opens a VeraCrypt-specific decryption interface.
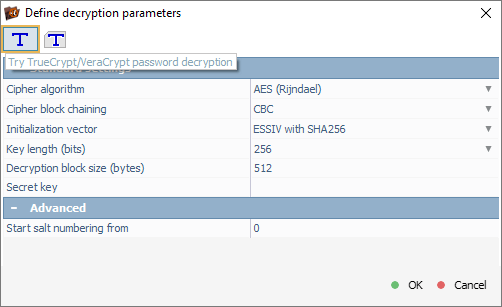
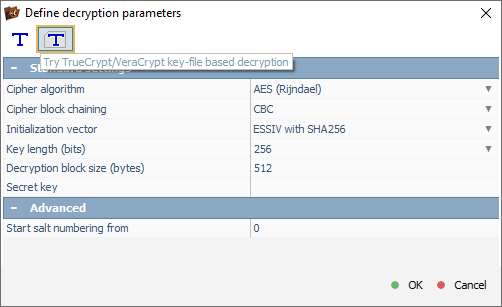
If a keyfile had been used to protect the volume, we would instead select the "TrueCrypt/VeraCrypt keyfile-based decryption" mode to load the corresponding keyfile.
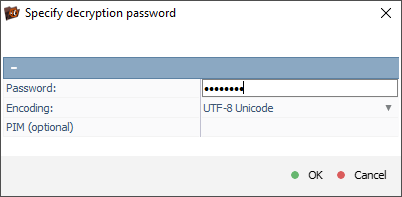
In the decryption dialog, we enter the password provided by the client and leave the PIM field blank, as no PIM was used.
Once we click "OK", UFS Explorer decrypts the volume and mounts it in a virtual mode.
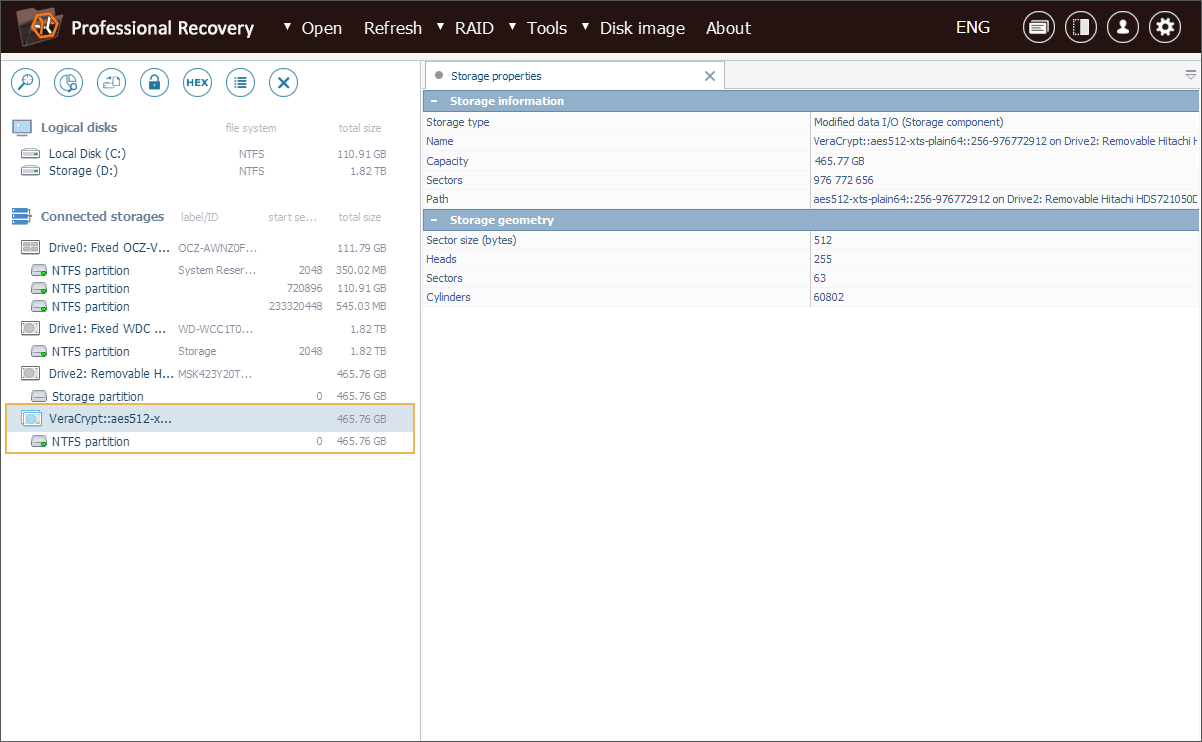
Now we can see the original NTFS file system found inside the encrypted container and proceed to scan it for deleted files using the program’s built-in recovery functionality.
Last update: September 17, 2025
